Data Protection Priorities Key on Compliance
GDPR - ISO 27000 Compliant
Sarbanes Oxley Compliant - HIPAA Complaint
Includes HIPAA Audit Program Guide &
ISO 27000 Security Checklist
Order Security Manual Template Download Sample
Data Protection Priorities Key on Compliance - Data protection priorities are impacted by various factors. Janco has identified seven of the ones that drive security policies and procedures
Order DRP BCP Security Bundle Download Sample
CIO and Executive Management Data Protection Priorities
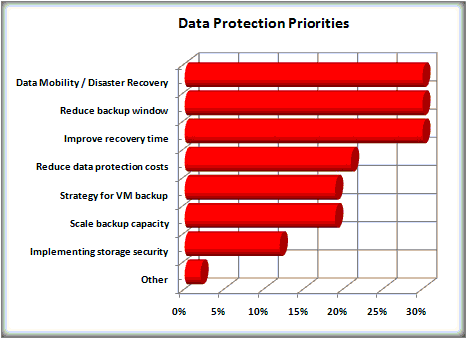
It's not just names and numbers anymore. CIO and executive management is now charged tp meet the data protection challenge head on with a new way to categorize sensitive data that helps you reduce data breach risk and take more control of your most critical assets. The top priorities are:
- Data Mobility
- Disaster Recovery - Business Continuity
- Reduction of the backup window
- Improved recovery time
- Strategy for virtual (cloud) backup
- Scalable backup up capacity
- Storage security
- Mandated requirements
Data Protection Policies and Procedures
The Security Manual for the Internet and Information Technology is over 215 pages in length. All versions of the Security Manual template include both the Business & IT Impact Questionnaire and the Threat & Vulnerability Assessment Tool (both were redesigned to address Sarbanes Oxley compliance). In addition, the Security Manual Template PREMIUM Edition contains 16 detail job descriptions that apply specifically to security and Sarbanes Oxley. The job descriptions are:
|
|
Clients can also subscribe to Janco's Security Manual update service and receive all updates to the Security Manual Template for 12 months* from the date of purchase.
The template includes everything needed to customize the Internet and Information Technology Security Manual to fit your specific requirement. The electronic document includes proven written text and examples for the following major sections for your security plan:
- Security Manual Introduction - scope, objectives, general policy, and responsibilities
- Risk Analysis - objectives, roles, responsibilities, program requirements, and practices program elements
- Staff Member Roles - policies, responsibilities and practices
- Physical Security - area classifications, access controls, and access authority
- Facility Design, Construction and Operational Considerations - requirements for both central and remote access points
- Sensitive Information Policy
- Media and Documentation - requirements and responsibilities
- Data and Software Security - definitions, classification, rights, access control, INTERNET, INTRANET, logging, audit trails, compliance, and violation reporting and follow-up
- Network Security - vulnerabilities, exploitation techniques, resource protection, responsibilities, encryption, and contingency planning
- Internet and Information Technology contingency Planning - responsibilities and documentation requirements
- Travel and Off & Site Meetings - specifics of what to do and not do to maximize security
- Insurance - objectives, responsibilities and requirements
- Outsourced Services - responsibilities for both the enterprise and the service providers
- Waiver Procedures - process to waive security guidelines and policies,
- Incident Reporting Procedures - process to follow when security violations occur
- Access Control Guidelines - responsibilities and how to issue and manage badges / passwords
- Sample Forms and Checklists
- Business and IT Impact Questionnaire
- GDPR Compliance Checklist
- Threat & Vulnerability Assessment Tool
- Security Violation Reporting form
- Security Audit form
- Inspection Check List
- New Employee Security form
- Security Access Application form
- Sensitive Information
- Employee Termination Checklist
- Supervisor's Employee Termination Checklist
- Sensitive Information Policy Compliance Agreement
- HIPAA Audit Program Guide
- ISO 27000 Security Checklist
Order Security Manual Template Download Sample










