IT Management Knowledge Base
CIO and IT Management Planning Tools
It is essential to have a proper backup strategy in place in case something goes wrong. Below are articles and links to tools that can help you in the Disaster Recovery and Business Continuity Planning and execution process. This knowledge base has been developed by Janco Associate, Inc.
- News Feed
- Make better and faster decisions
- Optimize the skills and opinions of all team members
- Minimize wasted time, energy, and resources
- Reduced wheel-spinning, ambiguity, and departmental politics
- Focus on critical results and outcomes
- Eliminated silos and focus on collective results
- Browse secured sites only.
- Use a VPN. This will protect traffic where it is most vulnerable, the last mile between a user and a server.
- Know what your vulnerabilities are and use tools needed to combat them.
- Keep your devices up-to-date with latest software.
- Be cautious about opening or replying to emails from unknown senders.
- With the move towards more mobile and office site computing users are challenged to keep their BYOD device safe and secure
- Purchase Android devices only from suppliers who release Android patches quickly.
- Implement the locking feature on all mobile devices
- Utilize applications on the device from the vendor (Apple or Google) application store
- When possible utilize two-factor authentication or bio metrics
- Use device encryption
- Connect to Wi-Fi via a Virtual Private Network (VPN)
- Utilize a Password management system
- Utilize anti-virus software
- Turn off un-used features like connections that are not used. If you don't use an application, uninstall it.
 Resume that is too long
Resume that is too long
- Resume that does not represent you in the best first impression
- Resume that is not structured well
- Resume that contains spelling errors
- Resume that contains grammatical and tense errors
- Resume that does not agree with your "social profile"
- Resume that contains a photo
- Resume that is not 100% accurate
- Resume that is the same for each job and company
- Not following up
WFH and Mobility Infrstructure Video Released
Management of IT functions driven by CIOs and enterprises' startegic direction
WFH and Mobility Infrstructure Policies 2024 Edition Released
WFH & Mobility Policy Bundle to Administer Telecommuters - The increasing use and dependency on IT is drastically changing the way companies improve employee productivity and keep in closer contact with its customers. Today most businesses provide laptops to employees. The challenge comes with Smart Phones and tablets while bringing additional benefits. Employees who are accustomed to using these tools in their personal life are requesting (or demanding) to use the same tools at the workplace.
Order WFH & Mobility Bundle Download Table of Contents
Project Manager - 6 steps to promotion
Project Managers are challenged to deliver results on time and with budget
Project Manager - 6 step to promotion in a fast paced environment.
Read on Proj Mgr Order Proj Mgr Job Description Sample Job Description
Mobile device security at risk due to CIO decisions
WFH - Mobile Device a Security Risk
The pandemic forced most companies to empty office buildings and move everything (and everyone) to WFH, remote locations and the cloud. Security shortcuts were taken because of the abrupt change to work from home and typically the transitions took place in a few days.
Also there were increased problems with IoT - especially as IoT devices in home environments accessed global systems via VPNs. This was the primary cause of spreading malware through the enterprise' information pipeline. A recent Verizon mobile security report reported, almost 50% of the users interviewed admitted that their company had knowingly cut corners on mobile device security.
AI is moving into the mainstream
UPS implements AI for delivery protection
UPS has implemented maching learning and AI to generate a delivery risk assessment based on two years of USP delivery data, historic loss patterns and address characteristics. It provides that data to retailers (including Amazon) to help determine the best delivery options.
The next move will be to add current data into the model and suggest to customers alternative delivery locations such as making it a "pick-up" from a secure location like a UPS store front.
Key Performance Indicators, Productivity, and Metrics
Key Performance Indicators, Productivity, and Metrics - KPI Metrics Quality Cost Control Products are all delivered electronically
Metrics are the key to productivity improvements. When the correct factors are measured - behavior is modified and encouraged resulting in improved productivity and operating performance. When the wrong things are measured there can, and offend are unintended negative consequences. Productivity can degraded as the wrong behaviors are encouraged. For this reason, it is critical for KPI to be driven by operational and strategic objectives.
Included in the KPI Metrics HandiGuide are proven KPI metrics which dozens of "World Class" enterprises have found create environments that are driven to succeed.
Our clients have found, many applications and application monitoring tools now depend on on-line desktop monitors with automated interaction with the system administrators to provide real time data analysis. In some cases these desktop KPI and metrics tools even operate on devices as small as a Smartphone.
Work From Home alters home requirements
Remote Work - WFH & Telecommuting environment
Remote work is reshaping the office products industry. Statista says sales of home office furnishings have increased dramatically since the pandemic began, with office chair sales up more than 75%. A recent survey by the National Association of Home Builders found that 63% of buyers include a home office in their list of requirements. USA Today reported that sellers of backyard sheds saw up to a 400% increase in inquiries last summer, as outbuildings became attractive workspaces.
Order WFH & Telecommuting Policy Download TOC
How to stay secure when you are traveling
Protect your data from lost and theft - Best Practices for International Travel
Man-in-the-middle attacks easy to pull off. At public Wi-Fi locations, the airwaves are open and any attacker with a simple antenna can mount an attack.
To improve overall online security:
Order Travel and Off-Site Meeting Policy Download Selected Pages
Top 10 Mobile Security Best Practices
Policies and procedures on how to deal with increasing mobility are the nemesis of CIOs around the world
Top 10 Mobile Device Security Best practices
Read On... Order WFH & Mobility Bundle Download Selected Pages
Top 10 Resume Mistakes
10 Things To Avoid In Your Resume
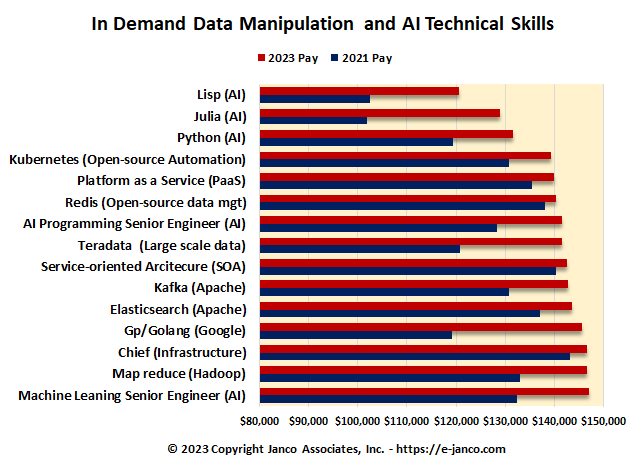
Top 15 In-Demand IT Technical Skils
Data Management, Data Manipulation and AI Technical Skills are in high demand
Janco has identified fifteen (15) skills that are the highest in demand. They are all related to data management, manipulation, presentation, and artificial intelligence (AI). The median compensation for these individuals is just under $140K. Plus many of these positions are in the Web3 arena.