CISO Job Description - Chief Information Security Officer
 Changing Role
Changing Role
Job Description - Chief Infomation Security Officer - CISO - Information and Data Security is an area that all enterprises are addressing. The primary objectives of the enterprise information and data security effort and the Chief Information Security Officer (CISO) are:
- Ensuring the confidentiality of sensitive information processed by, stored in, and moved through information systems and applications belonging to the enterprise. Examples of sensitive information processed by enterprise include personally identifiable information and other Privacy Act protected records; pre-release economic statistics; information provided by companies and individuals under the assumption of confidentiality; and pre-award contract financial information.
 Ensuring the integrity of the enterprise information such that decisions and actions taken based upon the data processed by, stored in, and moved through enterprise information systems can be made with the assurance that the information has not been manipulated, the information is not subject to repudiation, the source of the changes to information can be determined as best as possible.
Ensuring the integrity of the enterprise information such that decisions and actions taken based upon the data processed by, stored in, and moved through enterprise information systems can be made with the assurance that the information has not been manipulated, the information is not subject to repudiation, the source of the changes to information can be determined as best as possible.
- Ensuring the availability of the enterprise information systems and applications during routine operations and in crisis situations to support the enterprise Mission.
Chief Information Security Officers (CISOs) have many issues they must address when looking at overall security of the enterprise and the IT function. One of traditional ones is security monitoring. Security monitoring spans three areas of operations: monitoring operations (the running status); monitoring traffic (both in and out); and monitoring the results of use (keeping logs, statistics, and analysis). This encompasses monitoring physical hardware, server performance, services, and the network.
KPI Metrics for CISO include:
- Security Incident Rate: The incident rate indicates the number of security incidents that have occurred over a specific time period.
- Breach likelihood: Breach likelihood tells CISOs how likely they are to suffer a breach if the current attack trend continues.
- Cost per incident: Data breaches cost organizations their reputation and money.
- Risk exposure: Risk exposure is the product of breach likelihood and breach impact.
- Severity level of breach: The severity of a breach indicates its magnitude and the level of its devastation.
- Mean time to detect (MTTD): The MTTD tells CISOs how long it has taken their security team to detect a breach.
- Mean time to respond, recover, and resolve (MTTR): average time taken by the organization to return to its operational condition following a breach notification.
- Mean time to patch (MTTP): The MTTP is also referred to as the vulnerability patch response time.
- Training Level of security team: CISOs need to know how prepared their security team is to defend against cyberattacks.
Issues with Information and Data Security Monitoring:
- Determining what needs to be monitored
- No clear and holistic view of the data
- Too many - or too few - "agents" for the job
- Too many manual tasks
- Too much complexity and hidden costs
- Hodgepodge of low-end tools
IT Job Descriptions
The job descriptions created by Janco's executive consultants have taken these changes in role into consideration when the job description for the CISO was updated. The Chief Information Security Officer job description is over 4 pages in length.
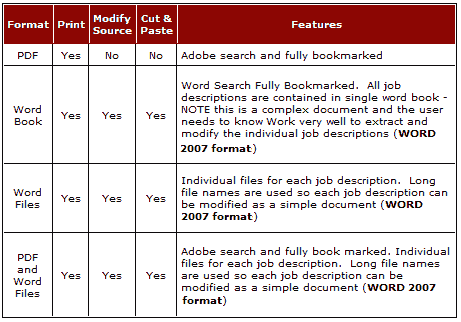
You can purchase this book as a PDF Book, Word Book or as individual word files for each Job Description (in Word .docx format) which makes for easier modification. We have also combined the both book formats with the individual word files for each job descriptions to give you the best of both worlds.
Order IT Job Description HandiGuide Sample Description Download TOC