Threat Risk Assessment Process
Process to manage the modification, distribution, and processes of data collection and summarization. . .
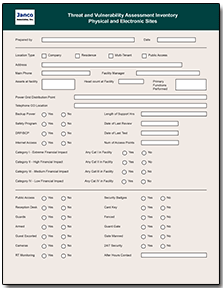
Read On Order Threat Vulnerability Assessment
Many individuals in any organization have useful information about how the organization functions, what is critical and what is not. You need to capture all of that information to make your assessment of the risk more thorough and effective. But remember, you are responsible for seeing that the assessment is carried out properly.
 The exposures are not only from traditional ones like fire, water, and smoke; but rather from internal and external hazards and threats, When thinking about your risk assessment, remember:
The exposures are not only from traditional ones like fire, water, and smoke; but rather from internal and external hazards and threats, When thinking about your risk assessment, remember:
- a hazard is anything that may cause harm, such as chemicals, electricity, working from ladders, an open drawer, etc; and
- the risk is the chance, high or low, that somebody could be harmed by these and other hazards, together with an indication of how serious the harm could be.
Janco's process includes five steps:
- Identify the hazards
- Decide who or what might be harmed or breached and how
- Evaluate the risks and identify potential solutions
- Record the findings
- Review the assessment and update if necessary
In many organizations, the risks are well known and the necessary control measures are easy to apply. You probably already know whether, for example, you have employees and areas that expose your organization to both internal and external threats. However you may not have categorized them. That is where Janco's Threat Risk Assessment Service can be of the greatest assistance to you.
This process relates and consoldates your cross functional risk assessment into one document to help you get started and save time.
- Obtain an Enterprise License for Threat and Vulnerability Assessment tool
- Update the electronic forms to include your logo
- Create a costume URL for your forms which your employees will be able to connect to
- Manage the on-line collection process of your data over a six month period for up to 50 respondents - a greater number of preponderant and or extend period can be supported at an additional fee which is negotiable
- Provide weekly status reports
- When 80% of the data is collected we will create a Summary Risk Assessment Matrix with instructions for how you can update it.
- All of the data from respondents will provided to you in electronic format for each individual
Janco's threat, risk and vulnerability assessment is an objective evaluation of threats, risks, and vulnerabilities in which assumptions and uncertainties are clearly considered and presented. Part of the difficulty of risk management is that measurement of both of the quantities in which risk assessment is concerned - potential loss and probability of occurrence - can be very difficult to measure. The chance of error in the measurement of these two concepts is large. A risk with a large potential loss and a low probability of occurring is often treated differently from one with a low potential loss and a high likelihood of occurring. In theory, both are of nearly equal priority in dealing with first, but in practice it can be very difficult to manage when faced with the scarcity of resources, especially time, in which to conduct the risk management process.
Order Threat Vulnerability Tool Download Selected Pages




