Electronic Forms for Threat Assessment Toolkit Released
Performing a threat assessment involves identifying potential threats to an environment - Janco's Electronic Forms make that process easier
 Electronic Forms for Threat Assessment Toolkit Released - Assets have different risks associated with them, and organizations need to correlate risks with each of the assets in a company. Some risks will impact all of the assets of a company, such as the risk of a massive fire destroying a building and everything in it, while in other cases; groups of assets will be affected by specific risks.
Electronic Forms for Threat Assessment Toolkit Released - Assets have different risks associated with them, and organizations need to correlate risks with each of the assets in a company. Some risks will impact all of the assets of a company, such as the risk of a massive fire destroying a building and everything in it, while in other cases; groups of assets will be affected by specific risks.
Assets of a company will generally have multiple risks associated with them. Equipment failure, theft, or misuse can affect hardware, while viruses, upgrade problems, or bugs in the code may affect software. By looking at the weight of importance associated with each asset, you should then prioritize which assets will be analyzed first, and then determine what risks are associated with each.
Once you have determined what assets may be affected by different risks, you then need to determine the probability of a risk occurring. While there may be numerous threats that could affect a company, not all of them are probable. For example, a tornado is highly probable for a business located in Oklahoma City, but not highly probable in New York City. For this reason, a realistic assessment of the risks must be performed.
Your company and organization, in all probability, has performed an information security risk assessment or had one done by an outside party. In addition you have likely undergone an IT audit. Both of these activities are designed to help assess risk and put appropriate controls in place.
However, in order to fully understand the risks your enterprise faces, these activities need to include a threat assessment. A threat assessment focuses on the potential threat sources your organization faces. The process includes reviewing the threat landscape for ongoing, upcoming and rising threats, and mapping them to vulnerabilities in the organization's systems and processes. Then, the threat assessment can be combined with an information security risk assessment to help the organization prioritize the security controls it needs to prevent a threat agent from taking advantage of vulnerability.
Order Threat Vulnerability Tool Download Selected Pages
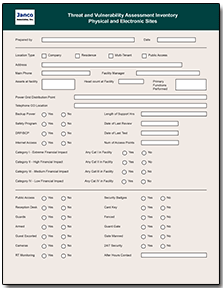
The Threat Vulnerability Assessment Tool
Janco's recently introduced Risk Assessment Electronic Forms facilitate this process and are an integral part of Janco's Threat Vulnerability Assessment Tool. With these forms it is now easier than ever to survey the threat and vulnerability landscape that your enterprise faces.Some of the drivers behind the Threat, Risk and Vulnerability Assessment Tool are requirements like those mandated by Sarbanes Oxley, HIPAA, ISO, and PCI-DSS.
For example, mandated compliance requirements necessitate enterprises conduct a risk vulnerability and threat vulnerability assessment. The process concludes with a security vulnerability assessment.
The hard work is done -- easy to use and implement
The Threat and vulnerability assessment process could not be any easier. The electronic forms come as fillable PDF forms or are available as part of on-line cloud based data collection process. In addition, Janco now offers a service where Janco will customize the forms for you, put them on-line, host the data capture, provide status on who has completed the form, and produce a summary Threat Assessment for a fixed fee.
With the extended service you are able to leverage the experience of one of the industry's leading experts and its clients to complete this critical process. The extended service includes:
- Enterprise License for Threat and Vulnerability Assessment tool
- Inclusion of your logo on the forms
- 2 hours of customization of form or consulting services
- Custom URL for your forms
- On-line collection of your data over a six month period for up to 50 respondents
- Data from respondents provided to you in electronic format
Service is Replaced by IT Governance Model
Read on IT Governance Infrastructure Strategy Order IT Governance Infrastructure Download Selected Pages
The tool is easy to use even if you have not experience in threat assessment or risk management. With the tool you:
- Establish the context of the threat and risks
- Create a risk rating matrix
- List the key risk areas
- Determining the likelihood and impact of the identified risks
- Determine current and required risk mitigation measures
- Develop a clear understanding the residual risk factor
Order Threat Vulnerability Tool Download Selected Pages




