 Security Audit Program a self administered proactive tool
Security Audit Program a self administered proactive tool
Addresses Ransomware, Work from Home (WFH), GDPR, ISO, HIPAA, SOX, and PCI-DSS - 2023 Edition
Security Audit Program CIOs can use as a benchmark - Many organizations have to respond to the queries of internal or external auditors and demonstrate that access to their unstructured data is being properly controlled. Questions such as the following from auditors are not uncommon:
- How do you know who can access this folder with financial/customer/sensitive data in it?
- Who authorized a user to have access permission to a file and how?
- If a key file was deleted, how would you know it happened, or who did it?
- Who were the last people to access a critical folder, and what did they do?
- How do you make sure that the right people have access to your data?
Order Security Audit Program Download Selected Pages
After years of regulation and embarrassing data breaches, the highest levels of management now comfortably discuss IT controls and audit results. However, their quality expectations are rising. Where IT once performed audits annually, many now support quarterly, monthly, and ad hoc exercises. Each audit expands the scope of the technologies assessed, measured, and proven compliant. Broader scope means more complexity and more work. With the Security Audit Program you can increase timeliness and accuracy of audit data while reducing IT audit effort, disruption, and cost.
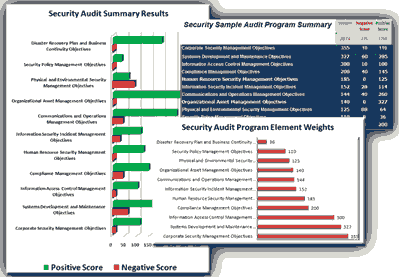 This Security Audit program contains over 400 unique tasks divided into 11 areas of audit focus which are the divided into 38 separate task groupings. The audit program is one that either an external auditor, internal auditor can use to validate the compliance of the Information Technology and the enterprise to GDPR, CCPA, ISO 28000 (Supply Chain Security Management System), ISO 27000 Series (ISO 27001 & ISO 27002), Sarbanes-Oxley, HIPAA, and PCI-DSS.
This Security Audit program contains over 400 unique tasks divided into 11 areas of audit focus which are the divided into 38 separate task groupings. The audit program is one that either an external auditor, internal auditor can use to validate the compliance of the Information Technology and the enterprise to GDPR, CCPA, ISO 28000 (Supply Chain Security Management System), ISO 27000 Series (ISO 27001 & ISO 27002), Sarbanes-Oxley, HIPAA, and PCI-DSS.
The 11 areas of audit focus and objectives are:
- Corporate Security Management
- Systems Development and Maintenance
- Information Access Control Management
- Compliance Management
- Human Resource Security Management
- Information Security Incident Management
- Communications and Operations Management
- Organizational Asset Management
- Physical and Environmental Security Management
- Security Policy Management
- Disaster Recovery Plan and Business Continuity
Included with this program are Microsoft (2003 and 2007 format) Excel workbooks and an indexed PDF document that contain the following:
- Read me - General instructions on the use of the Excel worksheets
- Audit Program Summary - Lists the 11 areas of audit focus and the 38 task groupings that are included within the audit. The point summary on this work sheet is calculated automatically by Excel.
- Audit Program Detail - Lists over 400 detail tasks the need to be completed in the audit and the relative point value of each task. The only thing that the user needs to do is check the yes or no on each item and re-assign a relative point value for each task.
- Audit Program Graphic - Lists the 11 areas of audit focus and a bar graph which shows the weights that are assigned to each area. The point summary on this work sheet is calculated automatically by Excel and the graph is automatically updated.
- Sample Audit Program - This is copy of the Audit Program Detail with data entered into the individual tasks.
- Sample Audit Program Summary - This is a copy of the Audit Program Summary with the links changed to point to the Sample Audit Program.
- Sample Audit Program Graphic - This is a copy of the Audit Program Graphic with links changed to point to the Sample Audit Program plus a chart has been added to show the positive and negative points of the audit. (see chart below)
Order Security Audit Program Download Selected Pages
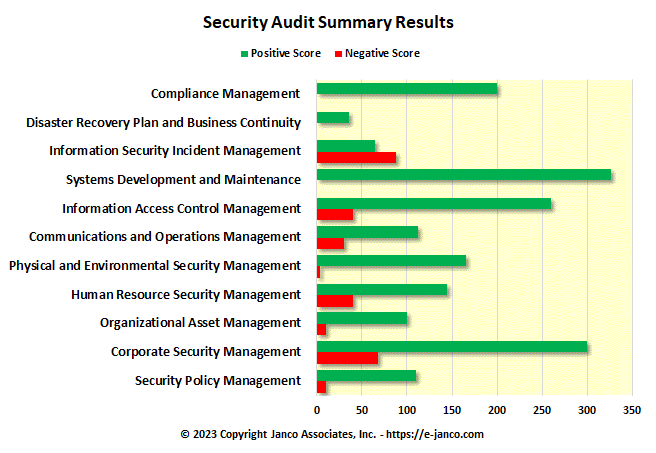
This is a summary graphic that was produced from the Excel worksheet provided as the Audit Program. In the sample above it is easy to see those areas where improvement is need.
Order Security Security Audit Program Download Selected Pages
Order Security Audit Program Download Selected Pages

 Security Audit Program - Self Scoring Tool
Security Audit Program - Self Scoring Tool  DR/BC Audit Program
DR/BC Audit Program




