Compliance Management Tool Kit - Defines Best Practices
PCI-DSS, Sarbanes-Oxley, HIPAA, GDPR,CCPA, GLAB, COBIT,
and ISO 28000 Compliance Tools
Order Compliance Management Kit Download Selected Pages
 Numerous laws and regulatory mandates focus on corporate governance and accountability around sensitive information (specifically financial, non-public information and protected health care information). This has significantly impacted the underlying IT systems that support the applications and repositories holding this sensitive information.
Numerous laws and regulatory mandates focus on corporate governance and accountability around sensitive information (specifically financial, non-public information and protected health care information). This has significantly impacted the underlying IT systems that support the applications and repositories holding this sensitive information.
Organizations are continuously looking for help in preventing fraud and protecting sensitive information. The fact that key corporate executives carry personal liability in the event of non-compliance virtually ensures compliance to be a key initiative in any large organizations. Additionally, there are other internal cost-containment requirements that can be effectively met by defining and implementing a sound auditing and compliance methodology. Most corporations agree that compliance leads to better corporate governance and management.
Compliance Management Toolkit Versions
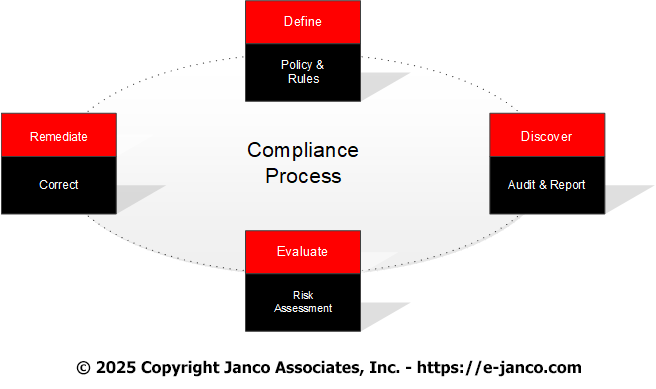
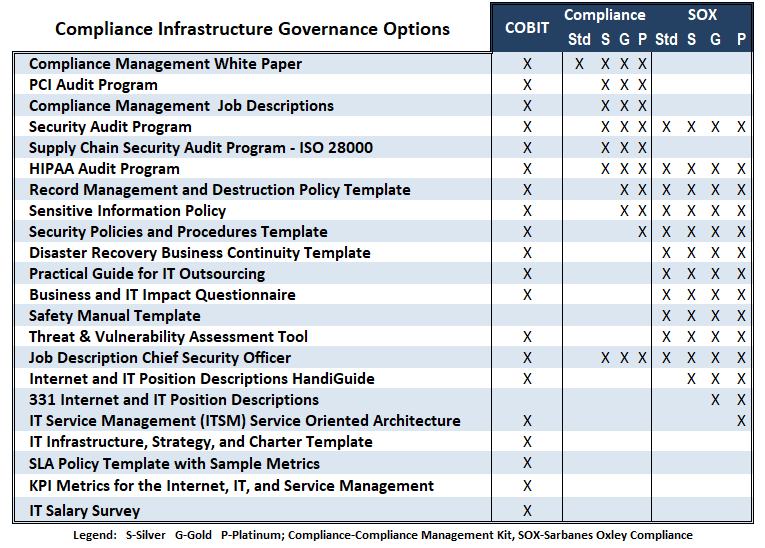
Janco offers a full range of tools to help enterprises of all sizes to address these issues. The Compliance Management kit provides necessary the infrastructure governance tools.
In addition to the Compliance Management White Paper we provided the The Compliance Management tool kit in three (3) versions: Silver, Gold, and Platinum.
Federal and state government regulations (see state compliance requirements) can be a big problem for today's organizations. There are more than 100 such regulations in the U.S. alone, and that number continues to grow. These are in addition to industry-specific mandates. They are all designed to safeguard the confidentiality, integrity, and availability of electronic data from information security breaches. So, what are the consequences if your organization fails to comply? Heavy fines and legal action. In short, it's serious.
Exposure for non-Compliance
Regulation |
Penalty |
Fine |
GLBA |
10 Years Prison |
$1,000,000 |
HIPAA |
10 Years Prison |
$100 per occurrence maximum of $25,000 per year |
| SOX | 10 Years Prison | $15,000,000 |
Sec Rule 17a-4 |
Suspension |
$1,000,000 |
GDPR |
none |
€10 million, or 2% of the worldwide annual revenue |
CCPA |
none |
$7,500 per record no cap |
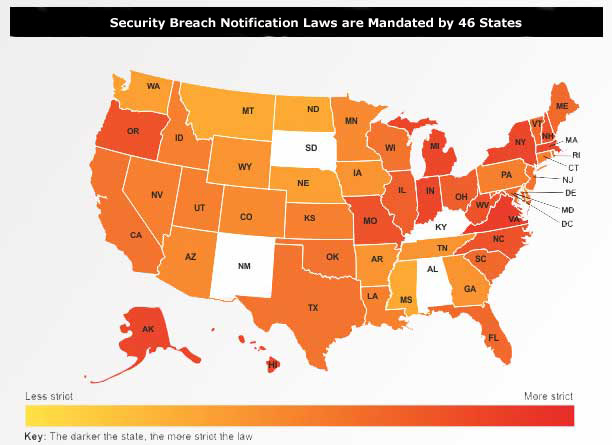
The graphic clearly depicts the magnitude of the current situation and the table provided by The National Conference of State Legislatures includes links to the individual states.The Security Manual Template address each of these mandate requirements.
Regulation
See Also Government Control of Internet
Order Compliance Management Kit Download Selected Pages