Cyber Insurance - Security Compliance
Cyber Insurance now more popular as ransomware attacks increase
Cyber attacks are on the rise. C-Level management from the CEO to the CIO are looking for solutions and protection. One protection is insurance to help recover the cost of restoration and ransomware payments. Insurance may not be what is advertised as insurance companies try to minimize payouts that they have to make.
Janco has identified shortfalls in recovery payouts from Cyber Insurance that companies have seen in a survey of 316 companies that had applied for a payout due to a cyber attack.
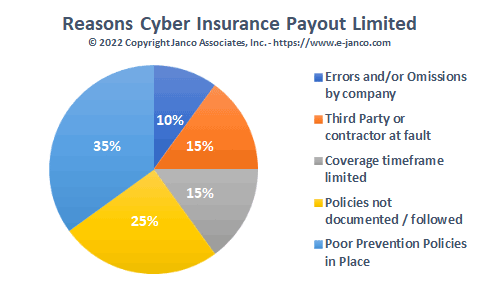
Reasons why Cyber Insurance payouts are reduced
-
Poor Prevention Policies in Place (35%) - Insurance policies typically state clients must have working policies in place that minimize cyber attacks. Some even state in their policies that companies install security software and procedures. This includes frequent security scans of the network and infrastructure for security threats. Also included is to change passwords, and have two-point user authentication and verification to secure servers and data.
-
Policies not documented/followed (25%) – One of the first things an insurance company asks for is copies of procedures and audits of cyber security for the enterprise. These need to be current and processes for changes, education, and compliance need to meet at least all mandated compliance requirements.
-
Coverage timeframe limited (15%) – A standard requirement is that the source of the breach occurred after the start of the coverage. Also, the coverage typically has a definition of what is included and excluded in the coverage. Unfortunately, companies with ransomware coverage are finding that cyber policies are not always the silver bullet they expected.
-
Third-Party or Contractor at Fault (15%) – If there is a security lapse at your cloud or network third-party provider, insurance companies are inclined to not pay the full amount. They can require that you seek reimbursement from them. Also if external contractors are involved in your enterprise's security they need to have coverage if they can be at fault in any way.
-
Errors and/or Omissions by the company (10%) – Everything needs to be considered. For example, the process of removing passwords for terminated employees and updating passwords and access points that are risky. Documenting your cyber security architecture and processes ahead of time will help to create an undeniable claim for maximum payout. Reporting, coupled with detailed compliance, is essential in recuperating costs from an attack. The documented evidence should include everything you have done to abide by the terms put forth by the insurer.
Compliance Process
The compliance process needs to be structured and robust enough to deal with all of the changing compliance requirements.
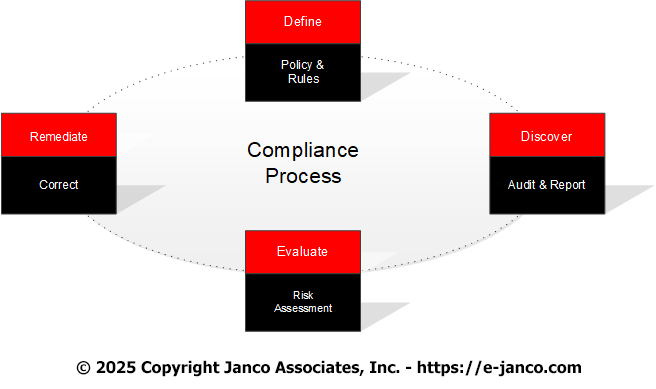
Best practices to meet compliance requirements are to have a compliance process in place that will not only define how compliance will be implemented but also to discover when compliance rules are no being followed. Then there needs to be a Risk Assessment to evaluate risks that exist. Finally, there needs to be a way to mitigate risks by re-meditating the identified risks. The tools listed below support this process.
Read on Order Security Manual Template Download sample


