Top 10 Cloud Security Vulnerabilities Identified

Cloud processing adds new vulnerabilities to the security and compliance landscape
The need to lower cost, increase efficiency and conserve cash has increased the motivation of companies to turn to Cloud Computing and increased the appeal of alternative delivery models.
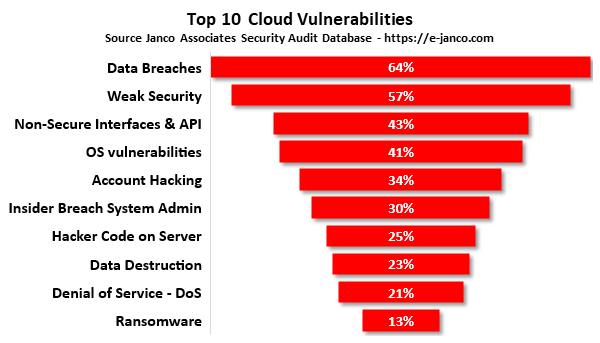
Top 10 cloud security vulnerabilities have been identified by Janco Associates from a series of cloud security compliance audits and reviews with CTOs, CIOs and CSOs on cloud security concerns.
- Data breaches - A data breach occurs when any information that is not intended for public release, including personal health information, financial information, personally identifiable information, trade secrets, and intellectual property is exposed. A data breach is not unique to cloud computing, but it is as a top concern for cloud users.
- Weak Security - Weak security allows cyber-criminals to act as legitimate users, operators, or developers that can read, modify, and delete data; issue control plane and management functions; spy on data. The root cause of this is insufficient identity, credential, or access control. An example is leaving a port open that allows access without authentication.
- Non-Secure Interfaces & API - Cloud providers typically provide a set of software user interfaces (UIs) or APIs to manage and interact with cloud services. These need to be designed to protect against accidental and malicious attempts to circumvent policy.
- OS vulnerabilities - OS vulnerabilities that allow attackers to infiltrate a system to steal data, taking control of the system or disrupting service operations. Vulnerabilities within the components of the operating system put the security of all services and data at significant risk. With multi-tenancy in the cloud, systems from various organizations are placed close to each other and given access to shared memory and resources, creating a new attack vectors.
- Account hijacking - Cloud services add a new threat to the landscape. If attackers gain access to a user’s credentials, they can eavesdrop on activities and transactions, manipulate data, return falsified information and redirect clients to illegitimate sites. For example when a cyber-attackers gains root level control of systems via an existing account.
- Insider breach as System Administrator - A disgruntled employee who is a system administrator can access potentially sensitive information, and can have increasing levels of access to more critical systems and eventually to data. Enterprises that depend solely on cloud service providers for security are at greater risk.
- Parasitic code on server - Parasitic code on server that infiltrates systems to establish a foothold in the IT infrastructure of target companies, from which they steal data. This type of code pursues its goals stealthily over an extended period of time, often adapting to the security measures. Once in place, they can move through data center networks and blend in with normal network traffic to achieve their objectives.
- Data Destruction - An accidental deletion by the cloud service provider, or a physical catastrophe such as a fire or earthquake, can lead to the permanent loss of customer data unless the the user takes adequate measures to back up data, following best practices in business continuity and disaster recovery.
- Denial of service (DoS) - DoS attacks are designed to prevent users of a service from being able to access their data or applications. Attackers can cause a system slowdown and leave all legitimate service users without access to services.
- Ransomware - Ransomware is malicious software, or malware, designed to deny access to a computer system or data until a ransom is paid. Ransomware typically spreads through phishing emails or by unknowingly visiting an infected website.
How to Guide for Cloud Process and Outsourcing
How to Guide for Cloud Processing and Outsourcing has as its primary focus provides everything that is needed to select a vendor, enter into an agreement, and manage the relationship.
Order Cloud Outsourcing Download Selected Pages