Is it time to have a National ID
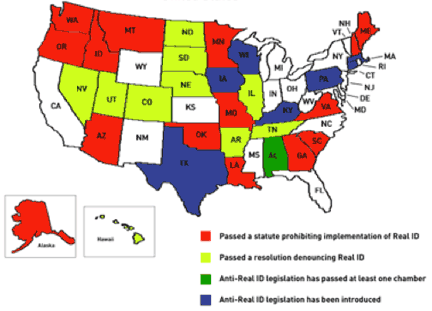
Is it time to have a National ID - What supporters hoped would be a seamless shift to a national ID card, has been impacted by various state legislatures which forbid their motor vehicle administration from participating - and could herald chaos at airports unrivaled by any other recent change to federal law. In addition compliance requirements would be impacted by all enterprises that store or use this information.
(added July 2018)
With the recent requirement for privacy requirements with GDPR and the California Consumer Privacy Act this now is a significantly more complex issue. The implication of a major breach on a National ID data base are even too onerous to contemplate.

Order Sensitive Information Policy Download Selected Pages Version History
If Home Land Security does nothing, air travelers from non-Real ID states would at least be subjected to what Homeland Security delicately calls "delays" and "enhanced security screening," or perhaps even be denied boarding. In addition, driver's licenses from non-Real ID states could no longer be used to access "federal facilities," including military academies, the Pentagon, Treasury Department, the U.S. Capitol, Veterans Affairs hospitals, and some federal courthouses.
Individuals with a driver's license from a state that is not materially compliant with Real ID would need to go through a secondary screening at airports and federal buildings.
Since its enactment, its backers have been aggressively defending Real ID, noting that many of the hijackers on September 11, 2001, were able to fraudulently obtain U.S. driver's licenses. Because Real ID links state DMV databases, establishes a standard bar code that can be digitally scanned, and mandates that original documents such as birth certificates be verified, backers claim the benefits extend beyond anti-terror and ID fraud cases. (Extending it to firearm and prescription drug sales has not been ruled out. )
Key to protection is a definition and implementation of security policies and procedures which meet all of the compliance requirements placed on enterprise. Once that is accomplished, a strict audit regiment needs to be implemented.
Janco has defined a set of tools which enterprises of all sizes can use to be prepared to protect against breaches and intrusion.
The Data Breach and Network Intrusion Detection Tools are the tools that are needed:
- Security Manual Template
- Security Audit Program
Order Sensitive Information Policy Download Selected Pages Version History