Cyberattacks are a major concern as technology advances
Cloud and Quantum Computing Causing Concerns
 Security concerns are on the rise as phishing emails, malware, and ransomware attacks increase. Hackers are stealing bank details, passwords, and other personal information. The Internet has provided malicious hackers with a variety of new ways to make money and cause disruption. Cloud and quantum computing are only exacerbating the problems.
Security concerns are on the rise as phishing emails, malware, and ransomware attacks increase. Hackers are stealing bank details, passwords, and other personal information. The Internet has provided malicious hackers with a variety of new ways to make money and cause disruption. Cloud and quantum computing are only exacerbating the problems.
Quantum computing has been viewed by many as a solution to managing security and infrastructure. Is that true? While quantum computing advances will bring benefits, they will also create new challenges. Most notably, the power of quantum computing can easily crack the encryption algorithms that have been used for decades to secure a range of areas, including on-line banking, secure communications, and digital signatures.
Today, quantum computing is expensive, and the expertise required to develop it is restricted to large technology companies, research institutions, and governments. But like any innovative technology, it will eventually become more commercially available and easier to access – and cyber criminals will be looking to take advantage of quantum.
State of Cyber Attack Technology
Currently, highly skilled cyber attackers are stealthily infecting victims with malware by abusing legitimate tools. The attackers attempt to stay under the radar by installing back-doors on appliances that didn't support security tools, such as SANS arrays, load balancers, and wireless access point controllers.
Victims become infected with malware which is used to deliver another form of backdoor malware which provides access to compromised machines, along with the ability to snoop on data stored or entered on systems.
The malware reads commands from legitimate logs, which are meant to record data from the OS, such as web pages and apps. In one scenario, the attackers can send commands to a compromised web server by disguising them as web access requests and, while the OS logs them as normal, the Trojan can read them as commands. The commands read by the malware contain malicious encoded files that are saved to an arbitrary folder and they run as a backdoor.
IT Infrastructure, Security, and Training need to be “beefed up”
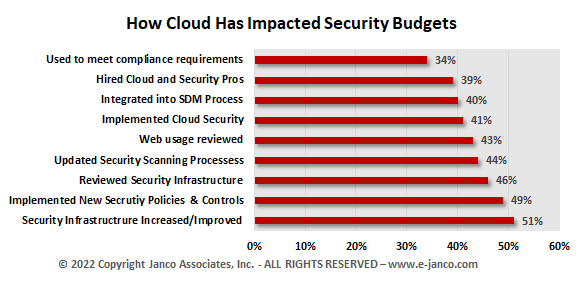
Cloud processing impacts capital, staffing, and operational budgets for security. In a recent review of the over 100 SMBs, Janco found that cloud processing has the greatest impact on security and IT operating costs in year-to-year comparisons.
The CIO's focus should on more than reducing costs and improving profitability. Security management and control need to be on that list. The Information Technology organization needs to get out of a transactional mode. If the CIO has the right infrastructure in place, then the CIO can help in directing the security and strategy of the enterprise, and even shape its destiny. The CIO brings their perspective and is a major contributor to the value added by the IT function.
Read On Order IT Infrastructure Policies Download Selected Pages