Top 10 Reasons Why Security Breaches Occur
With all of the concerns about security breaches, still one out of ten CIOs and CFOs feel they do not have an adequate security strategy in place and are reactive when an incident does occur. Many of them find out, the hard way, that the cost to react to an event is significantly greater than it would have been to implement an adequate solution before hand.
The top 10 drivers of security shortcomings include:
- Insufficient funding for security
- Lack of commitment by senior executive management
- Lack of leadership in the security arena by the CIO
- Belief that the organization will not be targeted
- Lack of internal resources who are "security" experts
- Lack of an effective IT security strategy
- Lack of an action plan on how to implement a solution before an event
- Infrastructure for IT that does not easily lend itself to security implementation including complex and disjointed applications and data
- No central focus with the enterprise that focuses on security
- Lack of a good termination policy for employees and contractors
With the move towards new technologies including cloud processing, social media, and employee personal devices, the risks a company faces will only continue to become greater in the future
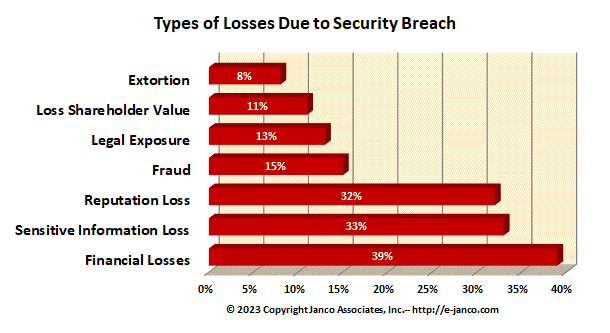
In reviews of security breaches of over 200 organizations Janco has identified several type of losses and impacts on companies. The cost of the "average" breach has been found to be well over $1,500,000. Categories of losses that companies face are:
- Financial loss - systems are down and revenue is halted and in many cases lost for ever
- Sensitive and confidential data is lost - not only can data be lost but confidential information can be made public and or available to competitors
- Reputation impacted - when a breach becomes public (which companies need to do based on compliance requirements) trust in lost in the company and its image can be forever tarnished.
- Fraud - many assets are "electronic" be they funds or intellectual property and individuals and companies can seek gain at the expense of the company that was preached.
- Legal exposure - when data is disclosed such as email, there can be damage that can impact an enterprise's liability.
- Loss of Shareholder Value - when a event occurs and it is adverse the stock price of publicly traded companies can fall and future revenues can be forever lost impacting the value of the company.
- Extortion - the latest trend is to high-jack a network and charge a ransom to unfreeze the applications and data assets of the enterprise.
In a review of over 200 incidents we have found the frequency of these types of breach losses to be as depicted in the chart below:
Read on Order Security Manual Template Download sample
Security Manual Template
This Security Policies and Procedures Manual for the Internet and Information Technology is over over 230 pages in length. All versions of the Security Manual template include both the Business & IT Impact Questionnaire and the Threat & Vulnerability Assessment Tool (both were redesigned to address Sarbanes Oxley and CobiT compliance). In addition, the Security Manual Template PREMIUM Edition contains 16 detail job descriptions that apply specifically to security and Sarbanes Oxley, ISO 27000 (ISO27001 and ISO27002),CobiT, PCI-DSS, and HIPAA. Data Protection is a priority.
Order Security Manual Template Download Sample

