ISO 28000 - Supply Chain Security - Guidelines for auditors on information security controls
2025 Edition IOS 28000 Supply Chain Security Audit Avaialbe for immediate download
 ISO 28000:2007 is necessary for support of an organization implementing and managing a Supply Chain Security Management System (SCSMS)
ISO 28000:2007 is necessary for support of an organization implementing and managing a Supply Chain Security Management System (SCSMS)
ISO 28000 - Supply Chain Security - With companies that have a high reliance on just-in-time delivery, aging infrastructure and increased natural and human-made threats. As a result Supply Chain Security has become a very important item for them, especially when viewed in relation with Business Continuity Management, Risk Management and Security Management.
Order Supply Chain Audit Program Download sample
ISO 28000 Definition
"This International Standard (ISO 28000) specifies the requirements for a security management system, including those aspects critical to the security assurance of the supply chain. Security management is linked to many other aspects of business management. Aspects include all activities controlled or influenced by organizations that impact on supply chain security. These other aspects should be considered directly, where and when they have an impact on security management, including transporting goods along the supply chain".
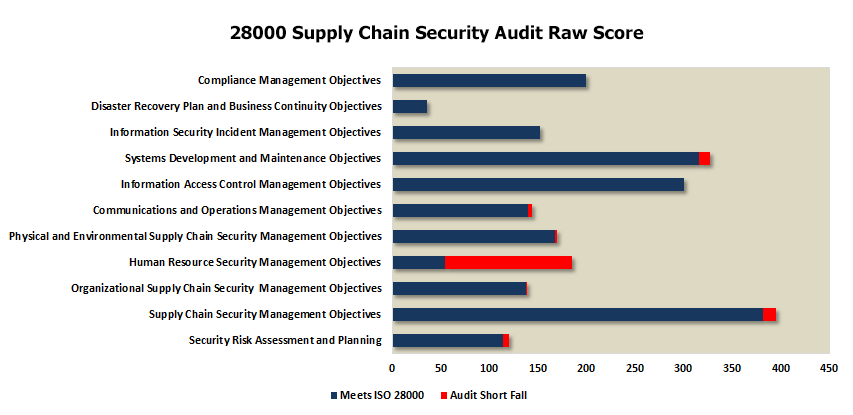
Supply Chain Audit program comes as an Excel Spread sheet that is 23 pages in length with 369 individual audit points covering:
- Security Risk Assessment
- Risk Assessment
- Supply Chain Security Management Objectives
- Internal Security Organization
- Implementation and Operation of Supply Chain Security
- Organizational Supply Chain Management Objectives
- Responsibility for Supply Chain
- Information Classification System
- Human Resource Management Objectives
- Security prior to employment
- Security during employment
- Security at termination
- Physical and Environmental Supply Chain Security Management Objectives
- Secure areas
- Enterprise equipment
- Remote Devices
- Communication and Operations Management Objectives
- Procedures and Responsibilities
- Third Party Service Delivery
- System Planning Activities
- Malicious and Mobile Code
- Backup Procedures
- Computer Networks
- Information Media
- Exchange of Information
- Interfaces (Blockchain)
- Information Access Control Management Objectives
- Access to Information
- User Access Rights
- Access Practices
- Access to Network Services
- Access to Operation Systems
- Access to Applications
- Mobile and Remote Users
- System Development and Maintenance Objectives
- Information System Application Security
- Applications Processing Information
- Cryptographic Controls
- System files
- Development and Support Processes
- Information Security Incident Management Objectives
- Security Events and Weaknesses
- Managing Security Incidents and Improvement
- Disaster Recovery Plan and Business Continuity Objectives
- DRP/BCP
- Compliance Management Objectives
- Mandated Security Requirements
- Security Compliance Reviews
- Information System Audits
Security Supply Chain Audit Program is easy to use and automatically generates graphics that can be used in management and compliance review presentations.
ISO 28000 was developed by the ISO Technical Committee TC8 "Ships and Maritime Technology". It is based on the ISO format adopted by ISO 14001:2004 because of its risk-based approach to management standards. The ISO 28000 series of standards consists of:
- ISO 28000:2007 - The Security Management Standard (SMS) requirements standard, a specification for an SMS against which organizations can certify compliance.
- ISO 28001:2007 - Provides requirements and guidance for organizations in international supply chains.
- Assists in meeting the applicable authorized economic operator (AEO) criteria outlined in the World Customs Organization Framework of Standards and conforming to national supply chain security programs.
- ISO 28002:2011 - Development of resilience in the supply chain - Requirements with guidance for use.
- ISO 28003:2007 - Requirements for bodies providing audit and certification of supply chain security management systems
- ISO 28004:2007 - provides generic advice on the application of ISO 28000:2007.
- ISO/AWI 28005 - ( Under development) Electronic port clearance (EPC) -- Part 1: Message structures.
- ISO/AWI 28005 - Electronic port clearance (EPC) -- Part 2: Core data elements
Order Supply Chain Audit Program Download sample