CIO and CSO Security Concerns With Increase in the number of Cyberattacks
CIO and CSO Security Concerns - Most Chief Information Officers and Chief Security Officers are concerned about security. There is good reason for this, we have found that when a "major" breach or incident occurs the CIO and CSO are the ones that take the brunt of the "blame" for the event. As a result, with 12 to 16 months those individuals are no longer in the roles they had.
Too many companies have found out the hard way that the most valuable assets they own are not their inventories, their petty cash drawer, or their company cars. Instead, the information about their business - payroll, customer records, sales prospects, business plans, patent applications - is the truly irreplaceable asset. Loss of a company's valuable information cannot be undone, and also often leads to significant damage to a company's reputation.
Order Security Manual Template Download Sample
Without constant vigilance, companies are vulnerable to attack. A necessary step is to assess your current security stance, then make a plan to increase security with proper best practices and technologies.
When we recently did our analysis of the top 10 CIO and senior management concerns, security got the top spot. It was followed by cloud processing and IT Infrastructure, both of which have an impact in the overall security of the data and application assets of the company.
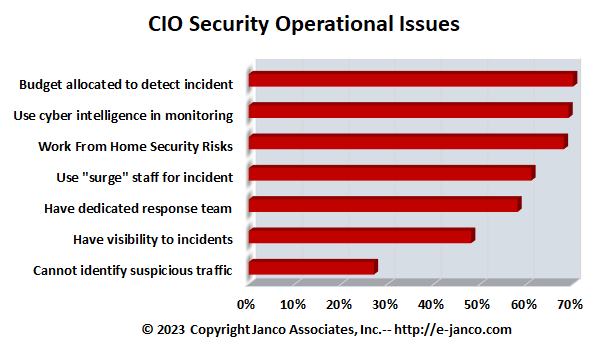
The top security management issues and metrics that we have found which address the security concern are:
- The dollar amount and percentage of the operational budget allocated to incident detection. Fully 30% of all organization do not have any budget at all allocated to this.
- Quality and availability of cyber-intelligence to use to monitor intrusions and minimize the number of false positives. We have found that on average organizations spend over $1,000,000 per year addressing false positives.
- Work From Home security risks and exposure of sensitive data with proper control and monitoring
- Availability and quality of a dedicated response team that can immediately address the incident and take remedial steps to stopping the further damage.
- Availability and quality of additional staffing resources, both internal and external, to be able to "surge" to an incident as it is occurring. All of the budget in the world will not help if the CIO or CSO cannot get the right resources are not identified before the event occurs.
- Ability to have visibility to incidents as they are occurring. The worst case scenario is one in which an incident occurs and is not discovered for some time magnifying the extent of the damage.
- Lack of ability and resources to segregate suspicious traffic from normal activity. When this happens a company only know that an incident has occurred after it is made public by someone other than the IT or security team.
Security Manual Template is a necessary step to address these concerns
This Security Manual Template is over over 230 pages in length. All versions of the Security Manual template include both the Business & IT Impact Questionnaire and the Threat & Vulnerability Assessment Tool (both were redesigned to address Sarbanes Oxley and CobiT compliance). In addition, the Security Manual Template PREMIUM Edition contains 16 detail job descriptions that apply specifically to security and Sarbanes Oxley, ISO 27000 (ISO27001 and ISO27002),CobiT, PCI-DSS, and HIPAA. Data Protection is a priority.
Order Security Manual Template Download Sample