Mobility Policy Bundle to Better Manage Remote Users

Note - this bundle has been replaced by the Work From Home and Mobility Infrastructure Policy Bundle
Policies and procedures on how to deal with increasing mobility are the nemesis of CIOs around the world - CCPA and GDPR implications addressed
Option to get a single PDF file containing all the polices at a discounted price
Order WFH & Mobility Bundle Download Table of Contents
Mobility Policy Bundle to Administer Telecommuters - The increasing use and dependency on IT is drastically changing the way companies improve employee productivity and keep in closer contact with its customers. Today most businesses provide laptops to employees. The challenge comes with Smart Phones and tablets while bringing additional benefits. Employees who are accustomed to using these tools in their personal life are requesting (or demanding) to use the same tools at the workplace.
In addition to the influx of mobile devices, companies are dealing with increasing numbers of employees who are working from non-traditional office locations. Whether employees are traveling, working from customer sites, or working from home, there is a growing need to access corporate data while outside the walls of an office and the firewalls of an IT department. Some questions are raised.
The policy helps enterprises:
Where should the focus be for mobility computing implementation? Supporting employees involves device management, the connection of those devices, and applications that support collaboration. While connecting with customers involves less focus on devices and more focus on applications and a support structure that addresses customer needs.
- Policies defined the rules of the road for mobile computing yet only one in five organizations have them defined and implemented. This lows rate of definition is driven by smaller to mid-sized firms as almost half of all large firms have mobility policies defined. The mobility policy template addresses all of the areas related to mobility: mobile devices (including procedures for lost devices), mobile applications including consideration for approved applications for business use), and data in mobile environments (including policy for using public WiFi networks).
- CIOs are looking into a wide range of devices. Most published data shows that the most capital expenditures are related to mobile devices - tablets (rising), laptops (declining), and Smart Phones (rising). A “post-laptop” era many not necessarily mean that laptops will disappear from the workplace. Rather Smart Phones and tablets can perform certain functions more efficiently than a laptop. Asides from communication, Smart Phones are mostly used for very light work, such as checking email or quick web browsing. Tablet users find a broader variety of applications, including note-taking and presentations. One implication is that CIOs will need to manage a suite of three devices for those workers who require flexibility in their computing options. Many CIOs are exploring mobile device management (MDM) tools, while others are adopting Bring Your Own Device (BYOD) policies by giving workers device stipends and transferring the liability and support away from the IT department.
- IT Help desks need to focus more of their resources handling mobile computing. Even though remote access is only available to one third of mobile workers and instant messaging is only available to one quarter, CIOs need to consider new technologies when providing support to workers who do not have ready access to in-person support options. Policies and performance metrics are a must.
- By definition, mobile devices are extending beyond corporate physical security controls and data on devices or transmitted over public WiFi networks is at risk. Security is a key concern for CIOs as they begin to implement mobile device solutions. Over two thirds of all CIO, according to Janco Associates, Inc. , feel that security of mobile devices is the largest risk to deal with when building a mobility strategy.
- Lost or stolen device are the most common type of mobile security incident today. How many times have we heard in the media that an employee of a hardware vendor loses a device in a bar or cab before it is released? Add to this, unauthorized applications or malware targeted at mobile devices that do put corporate systems at risk.
8 Policies included in the full bundle are:
- BYOD Policy
- Mobile Device Policy
- Privacy Compliance Policy
- Record Management Retention and Destruction Policy
- Social Networking Policy
- Telecommuting Policy
- Travel and Off site Meeting Policy
- Wearable Device Policy
- BONUS -- Chief Mobility Officer Job Description -- Just updated to reflect CCPA mandates
28 Electronic Forms included are:
- BYOD Access and Use Agreement Form
- Company Asset Employee Control Log
- Enterprise Owned Equipment Form
- Mobile Device Access and Use Agreement Form
- Mobile Device Security and Compliance Checklist
- Privacy Policy Compliance Agreement
- Safety Checklist - Working at Alternative Location
- Social Networking Policy Compliance Agreement Form
- Telecommuting Work Agreement
14 Full Job Descriptions including:
- Chief Mobility Officer
- Chief Security Officer
- Data Protection Officer
- Manager BYOD Support
- Manager Compliance
- Manager Security and Workstations
- BYOD Support Supervisor
- BYOD Support Specialist
- Security Architect
Order WFH & Mobility Bundle Download Table of Contents
Order WFH & Mobility Bundle Download Table of Contents

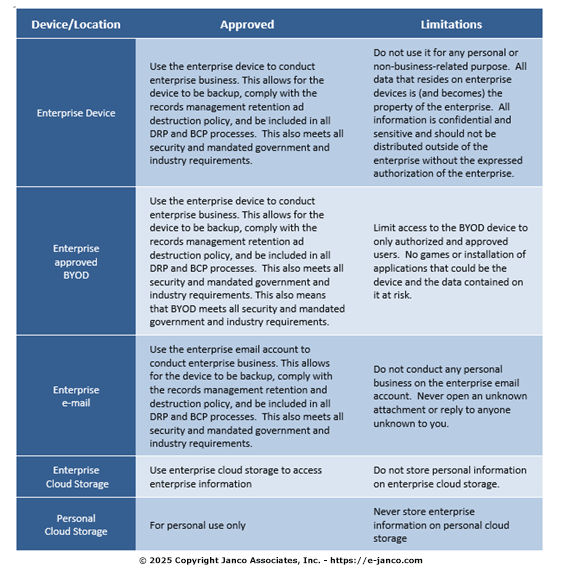



 There are many common myths about tape, disk, data protection and archiving, one, for example, being that archiving and long-term data retention are only for regulatory compliance purposes. The reality is that while regulatory compliance data, including Sarbanes-Oxley, ISO, financial or HIPAA medical, require long-term retention, many other common application data for almost every business, including those that do not fall under regulatory requirements, can benefit from - if not require - long–term data retention. The notion is to think beyond regulatory compliance. In other words, organizations of all sizes need and rely on information, both current and past.
There are many common myths about tape, disk, data protection and archiving, one, for example, being that archiving and long-term data retention are only for regulatory compliance purposes. The reality is that while regulatory compliance data, including Sarbanes-Oxley, ISO, financial or HIPAA medical, require long-term retention, many other common application data for almost every business, including those that do not fall under regulatory requirements, can benefit from - if not require - long–term data retention. The notion is to think beyond regulatory compliance. In other words, organizations of all sizes need and rely on information, both current and past. 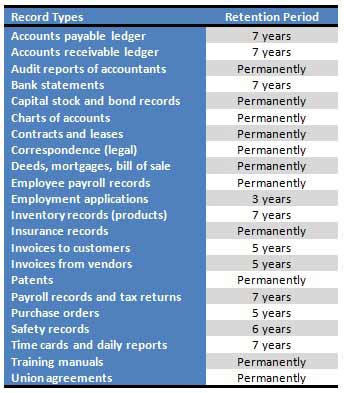

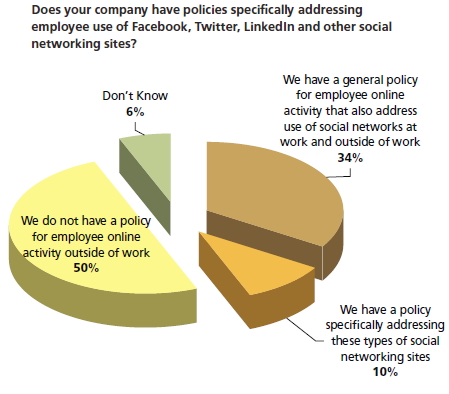
 WFH & Telecommuting is a popular alternative to making the drive in to work every day. If your users are asking about telecommuting to work, you may find that a telecommuting policy helps makes things clear to them.
WFH & Telecommuting is a popular alternative to making the drive in to work every day. If your users are asking about telecommuting to work, you may find that a telecommuting policy helps makes things clear to them. 









