Information Technology News Feed
Security, Disaster Planning, ITSM, Metrics, and Salary Survey
The Information Technology News feed is an XML news feed that you can subscribe to and re-publish on your web site or blog. The only requirement that you need to meet is that the feed is included with no modifications and that the links within the feed are retained as is.
If you wish to subscribe to this news feed the options that you have are:
- Information Technology News
- Insufficient funding for security
- Lack of commitment by senior executive management
- Lack of leadership in the security arena by the CIO
- Belief that the organization will not be targeted
- Lack of internal resources who are "security" experts
- Lack of an effective IT security strategy
- Lack of an action plan on how to implement a solution before an event
- Infrastructure for IT that does not easily lend itself to security implementation including complex and disjointed applications and data
- No central focus with the enterprise that focuses on security
- Lack of a good termination policy for employees and contractors
- Cloud-conscious attacks up by 110%
- Cloud environment inclusions up by 75%
- Number of victims named on eCrime leak /sites 76% on year-to-year analysis
- The number of attacks that had ransomware focus up by 84%
IT Governance Infrastructure Defined
Information Technology News Protal
IT Governance checklist and employee termination electronic forms
Information Technology is undergoing a rapid evolution as the importance of social media and the digital resources are changing the ways that enterprises operate, employees and enterprise associates interact on a day-to-day basis, and customers and suppliers access enterprise assets remotely.
The WFH options available for service centers and help desk support are driving change and IT infrastructure needs to adapt.
The CIO Infrastructure Management Tool Kit versions each contain some of essential tools that your enterprise needs as it creates budgets and sets priorities. The bundles include the IT Infrastructure, Strategy and Charter Template, Janco's latest IT salary data, the Business Impact and Application Questionnaire, Service Level Policy Template with sample metrics, Functional Specification Template, and the Practical Guide for IT Outsourcing.
- IT Governance Infrastructure Defined
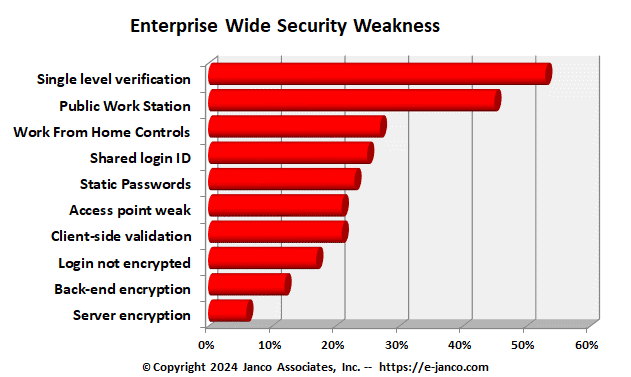
Top 10 Causes of Security Shortfalls
Security Manual Template Defines Best Practices
one out of ten CIOs and CFOs feel they do not have an adequate security strategy in place and are reactive when an incident does occur. The top 10 reasons for security shortfalls are:
Janco reviewed of over 200 incidents found the frequency of these types of breach losses:
Order Security Security Audit Program Download Selected Pages
- Top 10 Causes of Security Shortfalls
49 million customers face Dell data Breach
Security Policies and Procedures - First Step in Data Breach Protection
Data breaches will happen. Security and data breach protection are a never-ending process and that no CIO or CSO can claim that their data is completely secure.
The sheer number of data breaches reported this year alone has led to security experts dubbing this year as the "Year of the Hack. " What's an organization to do when the major technology companies are admitting they have been breached? With sophisticated malware, advanced attacks and sneaky insiders, security seems like an unattainable goal. Security is everyone's responsibility, from the board of directors, c-level executives such as the CEO, CIO, CFO, down to the front-line employees who actually work daily with sensitive information.
Dell Breach
The stolen data consists of about 7 million individual/personal purchase data, with 11 line items of consumer segment company data.
The impacted database contained entries from enterprise clients, partners, educational, institutions, and other entries. A hacker has posted the data is up for sale to a single buyer for an undisclosed amount.
There were implications in the post that the data might also consist of some sensitive information. "I don't have email/phone for this 49 million but I do have email & phone number of some several thousand other customers. All recent", the hacker posted.
Order Security Manual Template Download Sample
- 49 million customers face Dell data Breach
2024 Edition of Outsourcing and Cloud-Based File Sharing Policy Released
Includes seven full job descriptions and four electronic forms
Outsourcing and Cloud-Based File Sharing do not remove the enterprises requirement to manage the process or the data. Even a comprehensive outsourcing and cloud-based file-sharing arrangement requires Service Level Agreement (SLA) monitoring and redefinition, as well as strategic management and other retained functions. The policy address these issues as well as proving a basse to prevent costly cyber attacks.
Cyber attacks rose by over 30% in 2023. Global Threat report by Crowdstrike reported the types of attacks were
They also reported that the problem was not malware rather there was an increase in the number of attackers. Some were state-sponsored and others originated in countries that were not averse to providing cover for the attackers as 61% of attackers targeted the US and 11% targeted Europe.
Countries that were sources of those attacks were Russia, China, North Korea, Syria, Iran, Pakistan, Georgia, Columbia, and Turkey.
Order Outsourcing and Cloud Policy Download Selected Pages
- 2024 Edition of Outsourcing and Cloud-Based File Sharing Policy Released
Not a good idea to depend on Tech Giants Products
Tech Giants cannot be depended on rather IT Infrastructure Policies and Procedures are the solution
Tech Giants will create new products that are linked to thier infratructure and if they do not create enough value, they will just abandon them. For example, Google is killing off Inbox, its experimental email app that's lived alongside Gmail for the past four years. The service is set to shut down for good this coming March.
When Inbox was announced in October of 2014, Google described it as something that was years in the making and a completely different type of inbox, designed to focus on what really matters.They also said it was designed for the problems we're going to see in the next 10 years. The company is sending the app away to its increasingly crowded virtual graveyard.
Companies and individuals need to depend on thier own infrastructure.
Read On Infrastructure Policies
- Not a good idea to depend on Tech Giants Products