IT Tools for Managers - CIO Management Toolkit
Disaster Recovery Planning, Job Descriptions, Salary Survey, Business Continuity, ITSM, SOA, Compliance, SOX, and HIPAA
 IT Tools for Managers - CIO Management Toolkit - The IT Tools feed is an XML news feed that you can subscribe to and re-publish on your web site or blog. The only requirement that you need to meet is that the feed is included with no modifications and that the links within the feed are retained as is.
IT Tools for Managers - CIO Management Toolkit - The IT Tools feed is an XML news feed that you can subscribe to and re-publish on your web site or blog. The only requirement that you need to meet is that the feed is included with no modifications and that the links within the feed are retained as is.
If you wish to subscribe to this news feed the options that you have are:
177,000 IT Pros were unemployed before the shut down
The IT-ToolKits.com website is a resource site for Information Technology management.
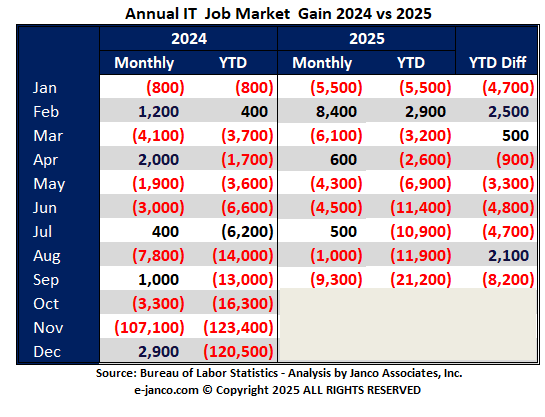
IT Job Market Change - September 2025
The number of employed IT Professionals continues to shrink, In September, before the shutdown, 9,300 jobs were eliminated. Over 177,000 professionals continued to be unemployed. Year to date 21,200 job were eliminated.
Read on IT Hiring Kit Order IT Hiring Kit
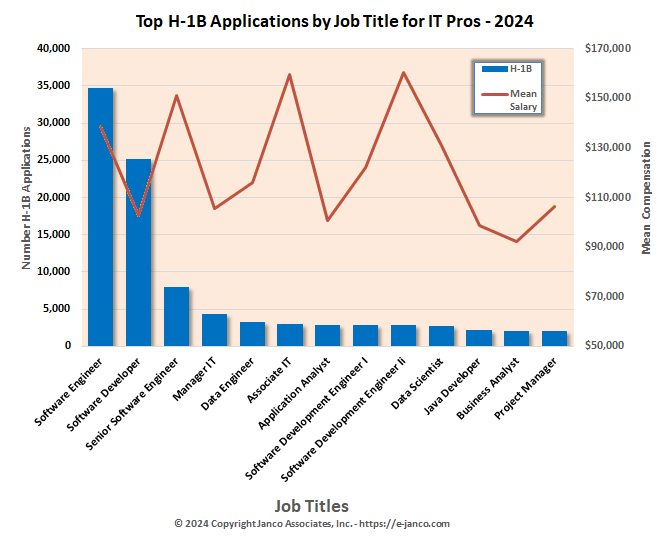
Impact of H-1B 100K fee
H-1B Visas fill many IT jobs - Impact of $100K Fee
Enterprise firms are already setting up in global tech hubs; startups and growth companies are turning to EOR services for compliant, distributed workforces. This isnt just about immigration; its about the future of how companies build global teams. EOR is on track to become the default option worldwide, reshaping the very definition of where work happens,.
Victor Janulaitis, CEO of IT management consultancy Janco Associates, said the $100,000 fee will accomplish two things: It will reduce the number of foreign national graduates from US Universities, and it will impact outsourcing companies like Tata Consulting Services in Mumbai, India, "which use the H-1 B program to displace US workers."
Order IT Job Description HandiGuide
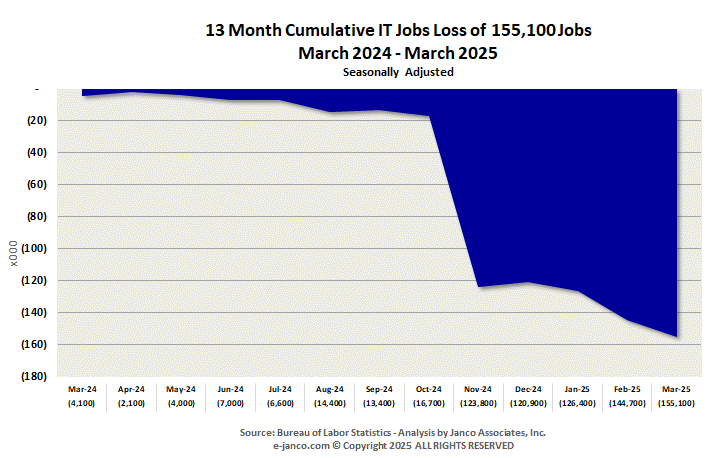
Hiring of IT Pros has has slowed
IT Pro unemployment rate is 5.0% - higher than the US National Unemployment rate
The United States' IT services sector saw a steep decline in employment in the first quarter of 2025, losing over 34,000 jobs as companies delayed spending on traditional services and leaned into artificial intelligence alternatives.
Read on IT Hiring Kit Order IT Hiring Kit
BYOD Policy UPDATE released
BYOD policy contains specific metric definitions for SLAs and a Balanced Scorecard
BYOD includes consumer SmartPhones and tablets, which are being used in your organization. Going mobile makes employees happier and more productive, but it's also risky. How can you say 'yes' to a BYOD choice and still safeguard your corporate data, shield your network from mobile threats, and maintain policy compliance?
Policy Template that addresses these issues and provides solutions for the following questions:
- What are the legal implications of BYOD?
- What is the impact of the Stored Communication Act - Record Retention and Destruction?
- What happens to the data and audit trail on a BYOD when an employee leaves the company?
- What about a lost or stolen BYOD?
- How is the BYOD configured to receive and transmit corporate data?
- What kind of passwords are acceptable to use on a BYOD?
- What kind of encryption standards are acceptable for BYOD?
- What types of BYOD are allowed and what types are not?
- What about jailbroken, rooted, or compromised BYOD?
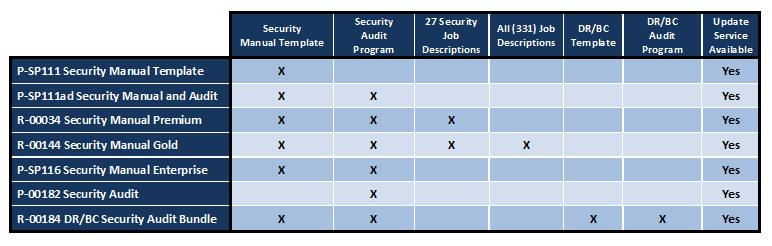
2025 Security Manual Released - AI Security Management - GDPR Compliance
Security Policies - Procedures - Audit Tools - AI Security Management - Supply Chain Security Management
Many organizations fail to realize the benefits of security information management due to the often exhaustive financial and human resource costs of implementing and maintaining the software. However, Janco's Security Manual Template - the industry standard - provides the infrastructure tools to manage security, make smarter security decisions and respond faster to security incidents and compliance requests within days of implementation. The template offers a framework for evaluating SIM services and shows how they could be applied within your organization.
Address issues like AI Security Management, Work From Home (WFH) operational requirements, Identify Protection, and SIEM (Security Information and Event Management). It is the complete must have tool. Also includes a ready-to-use Supply Chain and HIPAA audit programs.