CTO - CIO Management Articles
Security, Disaster Planning, ITSM, Metrics, and Salary Survey

The CTO Toolkits News feed is an XML news feed that you can subscribe to and re-publish on your web site or blog. The only requirement that you need to meet is that the feed is included with no modifications and that the links within the feed are retained as is.
Read on Chief Technology Officer Order CTO Job Description
The RSS newsfeed is:
Security Manual Template Released
Chief Technology Officer Productivity Tools - including CTO job description
Security Manual Template - 2025 Edition Released
Latest version of the Security Manual Template has been released. New features include:
How to Implement AI into Security Management
- Chief AI Officer job Description
- SIEM (Security Information and Event Management) which includes BEST PRACTICES and KPI METRICS
- Chapter on Identity Protection and what enterprises need to do to protect their users.
- PDF version that can be shared on tablets and smartphones25 electronic forms that support mandated compliance requirements.
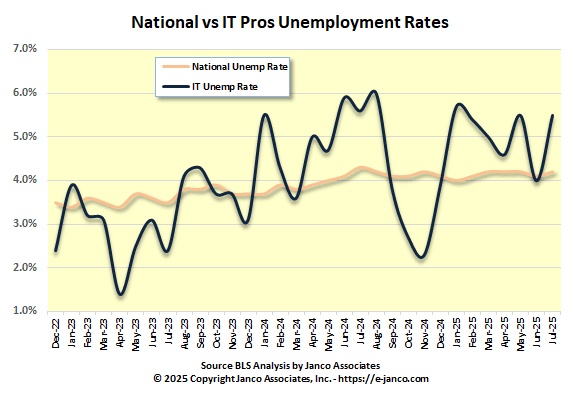
US National Employment is lower than IT Unemployment Rate
US National Employment is lower than IT Unemployment Rate
IT Job Market shrinks for 4 years in a row
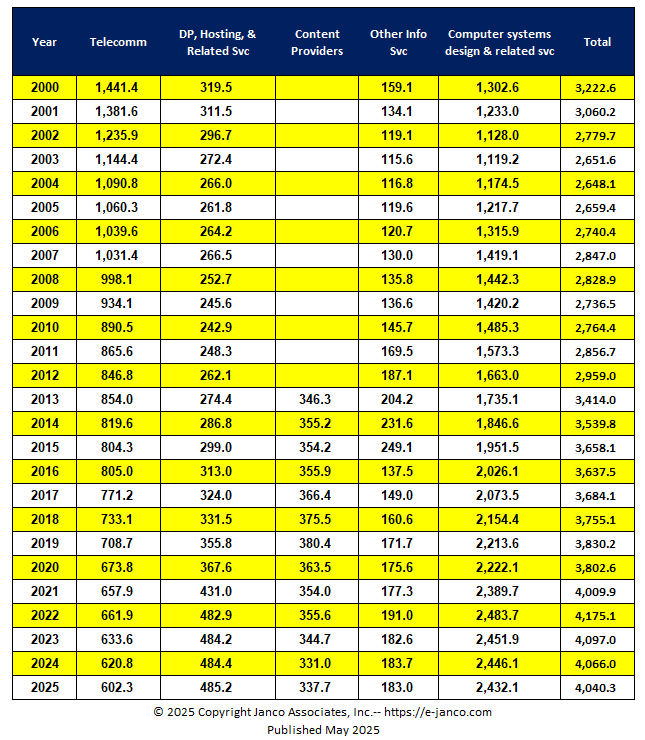
Historic IT Job Market Size
Blog and Personal Website Policy RELEASED
BLog and Personal Website Best Practices Defined
It is well known that blogging is one way to easily add new content to a website, and a number of corporate are embracing the idea with gusto. Not only are there companies that do allow corporate blogging, but in lots of cases it is not just the CEO or the marketing manager who blogs, but the actual employees of the company itself. A blog policy is a must.
It is clear that companies that venture into the corporate blogging arena would be wise to draw up blogging guidelines and have a formal blog policy. The blog policy should state clearly the boundaries within which the employee should operate, but it should not be so strict as to stifle any creativity or place a complete ban on the activity, nor make it so cumbersome to get permission to say something that it becomes virtually impossible to keep a personal feel to the blog and it merely becomes another official corporate mouthpiece.
Chief Artificial Intelligence Officer Job Description