Newsletter Topics
- Disaster Recovery Business Continuity Best Practices
- Business Continuity Planning 101
- Compliance Kit Updated
- IT Infrastructure Management - Premium Edition has 22 Electronic Forms
- CIO and IT Manager Productivity Tools
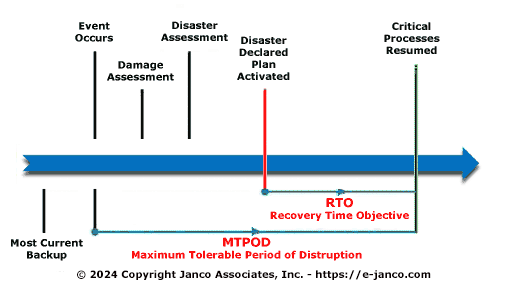
Disaster Recovery Business Continuity Best Practices
Best practices are the road to successful recovery after an event has occurred - seven rules to follow
- Focus on operations - people and process that drive the enterprise are the primary issues that DRP and BCP are controllable. Implementing a planning and recovery environment is an ideal time to define an approach based on ITIL best practices that will address the process and people issues effectively.
- Train everyone on how to execute the DRP and BCP - People are the front line when it comes to supporting the enterprise. A staff that has not been properly trained in the use of the DRP and BCP when an event occurs will we hindrance. Everyone must have the knowledge and skills to provide the right support. This not only helps reduce downtime, it also delivers better performance and a faster ROI through better and wiser use of IT assets.
- Have a clear definition for declaring when a disaster or business interruption occurs that will set the DRP and BCP process into motion - There needs to be a clear processes for allocating resources based on their criticality and availability requirements. This will define the “rules of the road” for who does what and when while minimizing the factors that can negatively impact enterprise operations.
- Integrate DRP and BCP with change management - Changes are inevitable in any sizable environment. It is difficult to keep up with the flood of new applications, technologies, and new tools. That is why it is essential to design, implement, and continuously improve change and configuration management processes.
- Focus on addressing issues BEFORE they impact the enterprise - When you are aiming to operate at the speed of business, after-the-fact fixes do not make the grade. These days, you need to anticipate trouble and head it off before it happens. It is important to identify risks across people, process, and technology so that appropriate countermeasures can be implemented. You should also make sure that vendors provide an appropriate level of support including proactive features such as critical patch analysis and change management support.
- Validate that all technology is properly installed and configured right from the start - a technology solution that is properly implemented in terms of its hardware, firmware, and software will dramatically reduce problems and downtime in the future. Proper initial configuration can also save time and reduce issues with upgrades, hot patches, and other changes.
- Monitor the processes and people to know what critical - many of today's enterprises are experiencing a capacity crisis as they reach the limits of reduced budgets, older facilities and legacy infrastructures. Space is tight. Power and cooling resources are over-burdened. Implementing new solutions in inefficient environments may limit their ability to recover from an event. An assessment that examines and analyzes the enterprises environment's capabilities and requirements can provide valuable information to help improve efficiency.
Business Continuity Planning 101
Many businesses have never tested the business continuity process in the event of a server or site failure
The basic process for developing a business continuity plan is:
- Create a business continuity planning team: Members should be from operations management, the chief security officer, the IT department, legal staff, and human resources.
- Define leadership roles: Determine which executives and employees are critical to operating the business (and supporting customers) that need to have access to key systems and information at all time.
- Assume the worst and plan for needed extra capacity: Before an event occurs, businesses need to plan ahead for increased network bandwidth and secured remote access requirements.
- Define emergency voice and data communications solutions: There are many to choose from, but a SSL VPN is one of the leading solutions to provide flexible, remote access, which is essential to any business continuity plan.
- Define access points for operations, network and IT: Create a business continuity portal for employees and partners. If the company has an Intranet, this site becomes command central from which employees can access information - HR policies, emergency contacts and a "start here" feature should be included.
- Contract for a secondary back-up site: Should the primary site be unavailable, companies should have a real-time mirror of data and staff housed at a secure facility.
- Backup data: In the event that the secondary site is unavailable, organizations should plan for multiple layers of failover.
- Plan to utilize smartphones and tablets: With mobile devices and “wireless networks”, IT departments can leverage these tools to ensure complete connectivity in times of emergencies.
- Pre-arrange Internet based meeting capabilities: In the event of an office closure, employees still need to communicate internally or with external parties (i.e. suppliers, customers). Implement the technology before it is needed
- Review number of sites and VPN gateways: Conducting an annual audit to provide a complete picture of your network and the ability to address problem areas before a disaster strikes.
- Test and test again: These ‘fire drills' enable the business continuity team to see how the current system is working, especially when employees are accessing information from remote locations (i.e. from home, a relative's house, and hotel). Once complete, those in management, IT and human resources can modify their business continuity plan accordingly.
All of this is defined in Janco's "Disaster Recovery - Business Continuity Template".
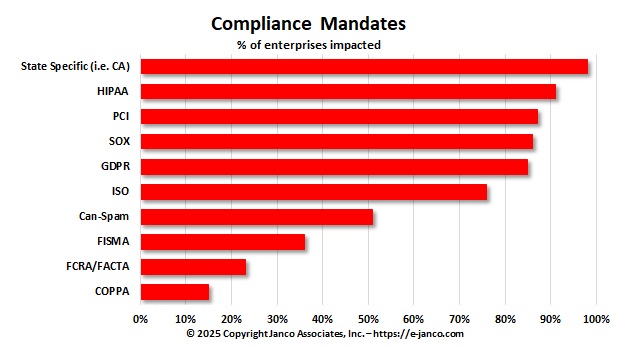
Compliance Kit Updated
 Compliance Program -10 Step program to follow
Compliance Program -10 Step program to follow
CIOs and CSOs are now under a great deal of scrutiny not only from their executive management but also from a range of governmental and industry regulatory bodies. Janco has created a ten step program that helps them address compliance issues directly. The program, when used in concert with Janco's Compliance Management products gets them in front of the issue.
More small and mid-sized business are impacted by state mandated (i.e. California, Massachusetts, New York, and others) than federal and SEC mandates.
Read On Order Compliance Management Kit Download TOC
IT Infrastructure Management -- Premium Edition Has 22 Electronic Forms
 In many enterprises, CIOs are perceived as mere technology managers, while in reality they should beviewed as business leaders. The CIO's focus should be on reducing costs and improving profitability through the strategic usage of IT. It is very important for the Information Technology organization to get out of a transactional mode. If the CIO has the right infrastructure in place, then the CIO can help in directing the strategy of the enterprise, and even shape its destiny. The CIO brings his own perspective, and without IT, you cannot build a robust and business.
In many enterprises, CIOs are perceived as mere technology managers, while in reality they should beviewed as business leaders. The CIO's focus should be on reducing costs and improving profitability through the strategic usage of IT. It is very important for the Information Technology organization to get out of a transactional mode. If the CIO has the right infrastructure in place, then the CIO can help in directing the strategy of the enterprise, and even shape its destiny. The CIO brings his own perspective, and without IT, you cannot build a robust and business.
The CIO Infrastructure Management Tool Kit is comprised of a collection of Janco products that CIOs and IT Managers can use to create a strategy and manage in the ever changing business environment.
Or you can get the CIO Infrastructure Policy Bundle which includes the following policies with Electronic forms. The policies have just been updated to comply with all mandated requirements and include electronic forms that can be Emailed, filled out completely on the computer, routed and stored electronically. A totally solution that uses technology at its best.
The policies have just been updated to comply with all mandated requirements and include electronic forms that can be Emailed, filled out completely on the computer, routed and stored electronically -- a total solution.
We have just completed a major update of all the individual polices and all of the electronic forms.
- CIO IT Infrastructure Policy Bundle (All of the policies below are included as individual MS Word files and a single PDF file. Electronic forms are all individual documents that are easily modifiable)
- Backup and Backup Retention Policy
- Blog and Personal Web Site Policy (Includes electronic Blog Compliance Agreement Form)
- BYOD Policy Template (Includes electronic BYOD Access and Use Agreement Form)
- Google Glass Policy (Includes Google Glass Access and Use Agreement Form)
- Incident Communication Plan Policy (Updated to include pandemic considerations and social networks as a communication path)
- Internet, e-mail, Social Networking, Mobile Device, Electronic Communications, and Record Retention Policy(Includes 5 electronic forms to aid in the quick deployment of this policy)
- Mobile Device Access and Use Policy
- Patch Management Policy
- Outsourcing and Cloud Based File Sharing Policy
- Physical and Virtual Server Security Policy
- Privacy Compliance Policy - California Privacy Act
- Record Classification, Management, Retention, and Destruction Policy
- Safety Program (Includes mandated OSHA electronic forms)
- Sensitive Information Policy (CCPA, GDPR & HIPAA Compliant and includes electronic Sensitive Information Policy Compliance Agreement Form)
- Service Level Agreement (SLA) Policy Template with KPI Metrics
- Social Networking Policy (includes electronic form)
- Technology Acquisition Policy
- Text Messaging Sensitive and Confidential Information (includes electronic form)
- Travel, Electronic Meeting, and Off-Site Meeting Policy
- Wearable Device Policy
- WFH & Telecommuting Policy (includes 8 electronic forms to effectively manage work at home staff)
- IT Infrastructure Electronic Forms
With Premium Edition - 22 Electonic Forms:
- Company Asset Employee Control Log
- Disaster Recovery - Business Continuity LAN Node Inventory
- Disaster Recovery - Business Continuity Location Contact Numbers
- Disaster Recovery - Business Continuity Off-Site Inventory
- Disaster Recovery - Business Continuity Personnel Location
- Disaster Recovery - Business Continuity Plan Distribution
- Disaster Recovery - Business Continuity Remote Location Contact Information
- Disaster Recovery - Business Continuity Team Call List
- Disaster Recovery - Business Continuity Vendor List
- Email - Employee Acknowledgement
- Employee Termination Checklist
- Internet & Electronic Communication Employee Acknowledgement
- Internet Access Request
- Internet Use Approval
- Mobile Device Access and Agreement
- New Employee Security Acknowledgement and Release
- Preliminary Security Audit Checklist
- Security Access Application
- Security Audit Report
- Security Violation
- Sensitive Information Policy Compliance Agreement
Read On Order ERP Job Descriptions Get Sample Job Description