Electronic Communication Policy - Email Rules
Internet, Email, Social Networking, Mobile Device, and Electronic Communication policy works in concert with Janco's other IT Infrastructure Tools

Electronic Communications Policy Template - Defining Your Optimal IT Infrastructure is a critical task that can no longer wait with all of the changes mandated by PCI-DSS, HIPAA, ISO, ITIL, Sarbanes-Oxley, changing economic environment, and changes to enterprise operating environments. Electronic communication is an intergral part of that infrastructure.
This policy has just been updated and includes twelve (12) electronic forms:
- Email Employee Agreement
- Internet Access Request
- Internet & Electronic Communication Agreement
- Internet Use Approval
- Security Access Application
- Social Networking Policy Compliance Agreement
- Telecommuting IT Checklist
- Telecommuting Work Agreement
- Text Messaging Sensitive Information Agreement
- Work From Home Contact Information
- Work From Home IT Checklist
- Work From Home Work Agreement
Order email communication Policy Download Policy Selected Pages
The policy helps enterprises:
- Understand and explain what infrastructure is, enabling enterprises, their constituents, and the executive team to manage the enterprise's technology environment more effectively;
- Analyze the current state their enterprise's infrastructure so they know where it works well and where to focus improvement efforts;
- Justify infrastructure spending, using the template's comprehensive definitions and ready to use examples to link IT infrastructure and the enterprise's bottom line; and,
- Prioritize enterprise resources with a prescriptive tool set that lets enterprises focus their efforts in a cost effective manner.
CIO IT Infrastructure Policy Bundle
 Save over 60% on these World Class Best Practices Policies
Save over 60% on these World Class Best Practices Policies
Janco has combine the policies that it has developed over time with some of the best IT organizations around the globe into a single package. With this bundle you get a PDF file that has all of the procedures in a single document that is over 210 pages long. It would take your staff months to develop these procedures from scratch. In addition you get a separate MS-Word document for each procedure which can easily be modified.
Order IT Infrastructure Policies Download Selected Pages
This bundle contains the following:
The policies have just been updated to comply with all mandated requirements and include electronic forms that can be Emailed, filled out completely on the computer, routed and stored electronically -- a total solution.
We have just completed a major update of all the individual polices and all of the electronic forms.
- CIO IT Infrastructure Policy Bundle (All of the policies below are included as individual MS Word files and a single PDF file. Electronic forms are all individual documents that are easily modifiable)
- Backup and Backup Retention Policy
- Blog and Personal Web Site Policy (Includes electronic Blog Compliance Agreement Form)
- BYOD Policy Template (Includes electronic BYOD Access and Use Agreement Form)
- Google Glass Policy (Includes Google Glass Access and Use Agreement Form)
- Incident Communication Plan Policy (Updated to include pandemic considerations and social networks as a communication path)
- Internet, e-mail, Social Networking, Mobile Device, Electronic Communications, and Record Retention Policy(Includes 5 electronic forms to aid in the quick deployment of this policy)
- Mobile Device Access and Use Policy
- Patch Management Policy
- Outsourcing and Cloud Based File Sharing Policy
- Physical and Virtual Server Security Policy
- Privacy Compliance Policy - California Privacy Act
- Record Classification, Management, Retention, and Destruction Policy
- Safety Program (Includes mandated OSHA electronic forms)
- Sensitive Information Policy (CCPA, GDPR & HIPAA Compliant and includes electronic Sensitive Information Policy Compliance Agreement Form)
- Service Level Agreement (SLA) Policy Template with KPI Metrics
- Social Networking Policy (includes electronic form)
- Technology Acquisition Policy
- Text Messaging Sensitive and Confidential Information (includes electronic form)
- Travel, Electronic Meeting, and Off-Site Meeting Policy
- Wearable Device Policy
- WFH & Telecommuting Policy (includes 8 electronic forms to effectively manage work at home staff)
- IT Infrastructure Electronic Forms
Blog and Personal Web Site Policy
 With the advent of blogs, there is a need to set rules of the road for the use of blogs by employees, contractors, agents, supplies and others. This 8 page sample blog policy contains specific policy statements on what can and can not be done via blogs. There are 13 specific guidelines defined as specific guidelines for personal web sites and blogs which are on your enterprise's domains and those on are on domains outside of your enterprise's control.
With the advent of blogs, there is a need to set rules of the road for the use of blogs by employees, contractors, agents, supplies and others. This 8 page sample blog policy contains specific policy statements on what can and can not be done via blogs. There are 13 specific guidelines defined as specific guidelines for personal web sites and blogs which are on your enterprise's domains and those on are on domains outside of your enterprise's control.
The policy template comes in word format and can easily be modified to meet the specific requirements of any size enterprise.
Mobile Device Access and Use Policy
 The purpose of this policy is to define standards, procedures, and restrictions for end users who have specific and authorized business requirements to access enterprise data from a mobile device connected via a wireless or unmanaged network outside of ENTERPRISE's direct control. This policy applies to, but is not limited to, all devices and media that fit the following device classifications:
The purpose of this policy is to define standards, procedures, and restrictions for end users who have specific and authorized business requirements to access enterprise data from a mobile device connected via a wireless or unmanaged network outside of ENTERPRISE's direct control. This policy applies to, but is not limited to, all devices and media that fit the following device classifications:
- Smartphones
- PDAs
- USB applications and data
- Laptop/notebook/tablet computers
- Ultra-mobile PCs (UMPC)
- Mobile/cellular phones
- Home or personal computers used to access enterprise resources
- Any mobile device capable of storing corporate data and connecting to an unmanaged network
The policy applies to any hardware and related software that could be used to access enterprise resources, even if the equipment is not approved, owned, or supplied by ENTERPRISE.
Mobile Device Access and Use Policy Template - This policy is 10 pages in length. It contains everything that an enterprise needs to implement a functioning and compliant mobile device and use process. Included are forms defining the mobile device environment.
Outsourcing and Cloud-Based File Sharing Policy
Outsourcing and Cloud-Based File Sharing Policy - This policy is 26 page in length and defines everything that is needed for function to be outsourced or the data to be shared via the cloud. The policy comes as a Microsoft Word document that can be modified as needed. The template has been updated to include a full audit program definition is 26 pages in length and covers:
- Outsourcing Management Standard
- Service Level Agreement
- Responsibility
- Outsourcing Policy
- Policy Statement
- Goal
- Cloud Based File Sharing
- Approval Standard
- Base Case
- Responsibilities
Included are two complete job descriptions in MS Word format -- Manager Outsourcing and Manager Vendor Management as well as two electronic forms -- Outsourcing Security Compliance Agreement and Outsourcing / Cloud Security Compliance Agreement.
Order Outsourcing Policy Download Table of Contents
Note: Look at the Practical Guide for Outsourcing, it is over 110 page in length and contains more extensive processes for outsourcing
Internet, e-mail, Social Networking Mobile Device, Electronic Communications, and Record Retention Policy
 Driving electronic communication is the fact that data is easier to find when it is a click away than when it is stacked in folders. E-mail is a great source of easy-to-access information. When faxes and paper communication are integrated into the email automation framework, there is little fear of losing them.
Driving electronic communication is the fact that data is easier to find when it is a click away than when it is stacked in folders. E-mail is a great source of easy-to-access information. When faxes and paper communication are integrated into the email automation framework, there is little fear of losing them.
Order email communication Policy Download Policy Selected Pages
Telecommuting
Organizations that have or want to establish a company wide telecommuting program should establish a formal, written telecommuting policy document that is regularly reviewed and updated by IT, human resources, legal, and finance. This will ensure that managers and the corporate services and technical support groups within the organization are aware of their respective role and responsibilities for enabling and supporting telecommuting. It also will help ensure that telecommuting employees know about their responsibilities too, along with new company and approved third-party applications and support services available outside company facilities.
Compliance Requirements
Businesses have to comply with industry-specific regulations for digital communications. This is a bigger challenge for multinational companies, where regulations vary from country to country. How can companies comply with these regulations without sacrificing business velocity and driving up costs? The answer lies in adopting standardized email policies that include best practice work flows to enforce compliance with industry-specific rules for process and content. This serves the dual purpose of keeping businesses out of trouble and providing superior customer experience.
Commercial Email
Best Practices for commercial Email are defined with compliance to CAN-SPAM Act as its focus.
Email Archiving
All companies archive e-mail whether they realize it or not. Merely backing up an e-mail server creates an archive. The real question is what policies your company should have regarding those archives. What messages should be archived, for how long, and who should be able to access them?
Depending on your requirements, which may or may not involve regulatory compliance, you can determine whether you need a separate e-mail archiving solution, and if so, what features it should have. In some cases, the features built into e-mail servers, which include e-mail retention policies and basic e-discovery capabilities, may be sufficient. In others, you may need to pay for a full-featured archiving system.
That may be money well spent if your risk is high. Financial penalties have been levied against companies not for any malfeasance, but simply for failing to comply with legal discovery or record-keeping requirements. Clearly, the costs of archiving would be more than offset in this situation.
Remember, however, that an e-mail archiving solution is not a substitute for a traditional e-mail backup and recovery solution. You still need the latter for e-mail reliability and availability. But the two can work hand in hand. E-mail archiving solutions feature additional benefits such as mailbox management, e-mail administration, and mail policy monitoring. Archiving can also help ease the burden on mail administrators, lowering overall costs by moving mail off of primary storage, pulling PST (Personal Storage Table) files off client systems, monitoring mail in real time for policy violations, and more.
Telecommuting threats
Today's email threats are far more dangerous than yesterday's. On the inbound side, blended email and web attacks masterminded by profit-seeking criminals are now the norm. Spam is no longer about selling, it's about stealing. Attacks are targeted and fast moving. The perpetrators are more sinister, organized, and sophisticated. Orchestrated botnet armies strike globally and quickly go dormant. Harmful payloads morph continuously to evade signature-based defenses, and are more often delivered through an embedded web link rather than a direct file attachment. Every malicious email that penetrates the perimeter carries dramatically more risk than ever before.
Order email communication Policy Download Policy Selected Pages
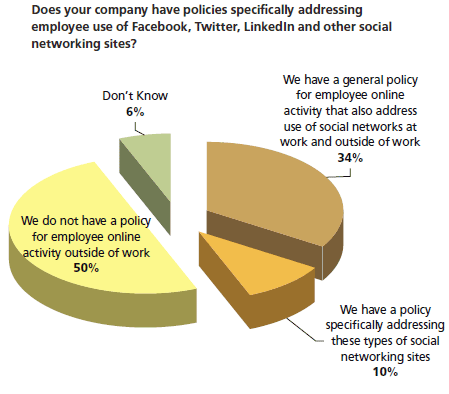
Over 50% of all companies do not have policies for the appropriate use of the Internet. The problem now is that when you Twitter or post to a blog information that might be sensitive thousands of people can see it immediately, and then thousands more could see it as it's forwarded on to others. The ramifications of making a mistake, of putting things that shouldn't be on there on those sites, are even greater than they used to be.
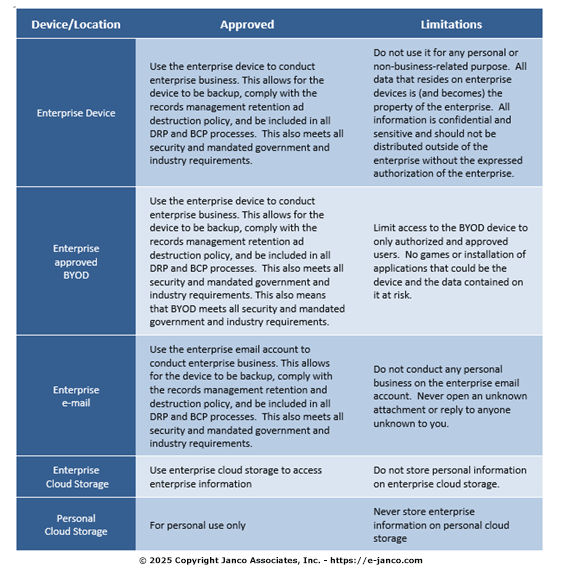
This policy is is compliant with all recent legislation (SOX, HIPAA, Patriot Act, and Sensitive information), and
covers: 
- Appropriate Use of Equipment
- Social Networks
- Mobile Devices
- Internet Access
- Electronic Mail
- Retention of E-mail on Personal Systems
- E-mail and Business Records Retention
- Copyrighted Materials
- Banned Activities
- Ownership of Information
- Security
- Sarbanes-Oxley
- Abuse
Included with the policy are forms that can be used to facilitate the implementation of the policy. Included are these ready to use forms:
- Internet & Electronic Communication Employee Acknowledgement
- E-mail - Employee Acknowledgement
- Internet Use Approval Form
- Internet Access Request Form
- Security Access Application Form
The WORD
template uses the latest CSS style sheet and can easily be modified
to conform to the style used in your enterprise policy manual.
Order email communication Policy Download Policy Selected Pages
Record Classification, Management, Retention, and Destruction policy
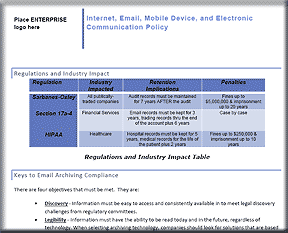
 There are many common myths about tape, disk, data protection and archiving, one, for example, being that archiving and long-term data retention are only for regulatory compliance purposes. The reality is that while regulatory compliance data, including Sarbanes-Oxley, ISO, financial or HIPAA medical, require long-term retention, many other common application data for almost every business, including those that do not fall under regulatory requirements, can benefit from - if not require - long–term data retention. The notion is to think beyond regulatory compliance. In other words, organizations of all sizes need and rely on information, both current and past.
There are many common myths about tape, disk, data protection and archiving, one, for example, being that archiving and long-term data retention are only for regulatory compliance purposes. The reality is that while regulatory compliance data, including Sarbanes-Oxley, ISO, financial or HIPAA medical, require long-term retention, many other common application data for almost every business, including those that do not fall under regulatory requirements, can benefit from - if not require - long–term data retention. The notion is to think beyond regulatory compliance. In other words, organizations of all sizes need and rely on information, both current and past.
Contains everything needed to implement a record management policy including an Interview Checklist to use when you are implementing a records management process
Order Record Management Policy Download Selected Pages Version History
A record is essentially any material that contains information about your company's plans, results, policies or performance. In other words, anything about your company that can be represented with words or numbers can be considered a business record - and you are now expected to retain and manage every one of those records, for slementing or altering the policy.
Several years or even permanently depending on the nature of the information. The need to manage potentially millions of records each year creates many new challenges for your business, and especially for your IT managers who must come up with rock-solid solutions to securely store and manage all this data.
The Record Classification, Management, Retention, and Destruction policy is a detail template which can be utilized on day one to create a records management process. Included with the policy are forms for establishing the record management retention and destruction schedule and a full job description with responsibilities for the Manager Records Administration.
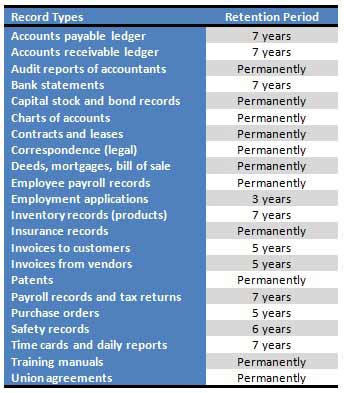
The areas included with this policy template are:
- Record retention requirements for SOX sections 103a, 302, 404, 409, 801a and 802.
- Policy
- Standard
- Scope
- Responsibilities
- Record Management
- Compliance and Enforcement
- E-mail Retention and Compliance
- Job Description Manager Record Administrator
- 12 forms for Record Retention and Disposition Schedule
- Record Management Best Practices
You can download the Table of Contents and selected pages for this policy template.
Order Record Management Policy Download Selected Pages Version History
Travel and Off-Site Meeting Policy
Travel and Off-Site Meeting Policy - Protection of data and software is often is complicated by the fact that it can be accessed from remote locations. As individuals travel and attend off-site meetings with other employees, contractors, suppliers and customers data and software can be compromised. This policy is sixteen pages in length (plus 4 electronic forms and 4 detail job descriptions) and covers:
- Laptop and PDA Security
- Wireless and Virtual Private Networks (VPN)
- Data and Application Security
- Public Shared Resources
- Minimizing attention
- Off-Site Meetings
- Remote Computing Best Practices
The job descriptions included are:
This policy has been updated to reflect the requirements of PCI-DSS, Sarbanes-Oxley, HIPAA, and ISO. The policy comes as both a WORD file and a PDF file utilizing a standard CSS style sheet.
Order Travel and Off-Site Meeting Policy Download Selected Pages
Sensitive Information Policy
Includes HIPAA Audit Program Guide, a PCI Audit Program, and an electronic form that can be used to quickly deploy this Policy. Plus as a bonus you get the User/Customer Bill of Rights for Sensitive and Confidential Information.
 This
policy is easily modified and defines how to treat Credit Card,
Social Security, Employee, and Customer Data. The template is 34
pages in length and complies with GDPR, Sarbanes Oxley Section 404,
ISO 27000 (17799), and HIPAA. The PCI Audit Program that is
included is an additional 50 plus pages in length.
This
policy is easily modified and defines how to treat Credit Card,
Social Security, Employee, and Customer Data. The template is 34
pages in length and complies with GDPR, Sarbanes Oxley Section 404,
ISO 27000 (17799), and HIPAA. The PCI Audit Program that is
included is an additional 50 plus pages in length.
This policy applies to the entire enterprise, its vendors, its suppliers (including outsourcers) and co-location providers and facilities regardless of the methods used to store and retrieve sensitive information (e.g. online processing, outsourced to a third party, Internet, Intranet or swipe terminals).
The HIPAA Audit Program Guide provides you with a checklist of the must be implemented items which HIPAA mandates.
You can download the Table of Contents and some sample pages by clicking on the link below.
Order Sensitive Information Policy Download Selected Pages Version History