State Mandated Compliance Requirements - GDPR - CCPA
Compliance Management Tools

Individual state data protection laws are unique in several ways. For example, Massachusetts has extended its reach well beyond its own borders by mandating data protection for its citizens regardless of where that data resides. On the other hand, most other state laws, do not define what methods shall be used (e.g. , encryption) to protect its citizens' data. In addition, the Massachusetts law provides for large civil penalties in the case of non-compliance, and opens organizations to seemingly unlimited civil action.
Order Compliance Management Kit Download Selected Pages
While it is not yet clear how this law will in fact be enforced, it is clear that any organization with customers in Massachusetts will be facing a tough new data protection environment. And as such, it behooves these organizations to start preparing now, to ensure not only compliance with this new law but to drive towards true data security and peace of mind.
To protect these types of sensitive data using identity management solutions, the following challenges must be addressed:
- Define and track changes to various policies, procedures and controls related to access rights.
- Track ongoing violations to the policies and processes related to access rights.
- Monitor the timeliness of violation or exception detection mechanisms and the corresponding remediation activity.
- Audit access activity for all resources hosting sensitive information.
- Analyze unauthorized attempts to access or change sensitive information.
- Analyze the incremental effectiveness of controls around access rights.
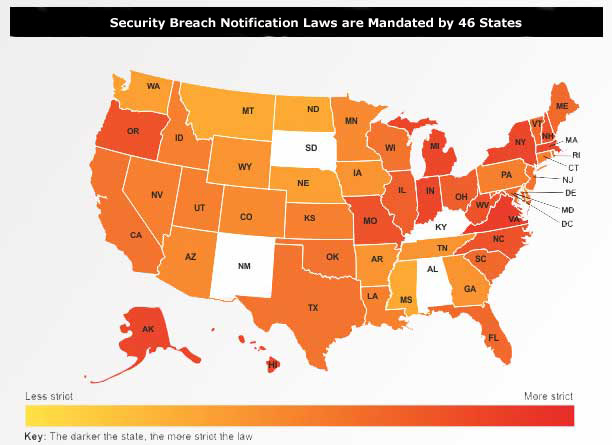
The graphic clearly depicts the magnitude of the current situation and the table provided by The National Conference of State Legislatures includes links to the individual states. The Security Manual Template address each of these mandate requirements.
California SB 1386 Personal Information Privacy
This regulation affects companies that do business with individuals living in California even if the ENTERPRISE is located outside of the state.
If unencrypted personal data is compromised, then ENTERPRISE must immediately disclose to the customer that a security breach has occurred.
Massachusetts Data Protection Requirements
Organizations that do business with Massachusetts residents must:
- Control passwords to ensure they are kept in a location and/or format which will not compromise the security of the data they protect
- Encrypt all personal information stored on lap tops or other portable devices
- Ensure reasonably up-to-date fire wall protection and operating system security patches, designed to maintain the integrity of the personal information
- Ensure up-to-date versions of system security agent software, which must include malware protection and up-to-date patches and virus definitions
- Have a Written Information Security Program (WISP) and to take “reasonable steps” to ensure that any third-party / independent contractors comply with these data protection provisions. (The Janco Security Manual Temple includes a detail check list and policy template that meets these requirements)
Compliance Management Tool Kits
Janco offers a full range of tools to help enterprises of all sizes to address these issues. The Compliance Management kit provides the infrastructure tools necessary address these mandated requirements.
The Compliance Management tool kit comes in three (3) versions: Silver, Gold, and Platinum. Plus you can save over $2,000 when you order the COBIT IT Governance Kit
Order Compliance Management Kit Download Selected Pages