DRP and BCP Best Practices
Proper DR BC planning is required for a successful recovery
A best practice for disaster planning and business continuity is a technique, method, process, activity, incentive, or reward that is believed to be more effective at restoring the operation of an enterprise after a disaster or enterprise interruption event occurs.
The idea is that with proper processes, checks, and testing, a desired outcome can be delivered with fewer problems and unforeseen complications. Best practices can also be defined as the most efficient (least amount of effort) and effective (best results) way of accomplishing a task, based on repeatable procedures that have proven themselves over time for large numbers of people.
Order DRP BCP Template DRP BCP Sample
Disaster recovery and business continuity best practices
- Focus on operations - people and process that drive the enterprise are the primary issues that DRP and BCP are controllable. Implementing a planning and recovery environment is an ideal time to define an approach based on ITIL best practices that will address the process and people issues effectively.
- Train everyone on how to execute the DRP and BCP - People are the front line when it comes to supporting the enterprise. A staff that has not been properly trained in the use of the DRP and BCP when an event occurs will we hindrance. Everyone must have the knowledge and skills to provide the right support. This not only helps reduce downtime, it also delivers better performance and a faster ROI through better and wiser use of IT assets.
- Have a clear definition for declaring when a disaster or business interruption occurs that will set the DRP and BCP process into motion - There needs to be a clear processes for allocating resources based on their criticality and availability requirements. This will define the “rules of the road” for who does what and when while minimizing the factors that can negatively impact enterprise operations.
- Integrate DRP and BCP with change management - Changes are inevitable in any sizable environment. It is difficult to keep up with the flood of new applications, technologies, and new tools. That is why it is essential to design, implement, and continuously improve change and configuration management processes.
- Focus on addressing issues BEFORE they impact the enterprise - When you are aiming to operate at the speed of business, after-the-fact fixes do not make the grade. These days, you need to anticipate trouble and head it off before it happens. It is important to identify risks across people, process, and technology so that appropriate countermeasures can be implemented. You should also make sure that vendors provide an appropriate level of support including proactive features such as critical patch analysis and change management support.
- Validate that all technology is properly installed and configured right from the start - a technology solution that is properly implemented in terms of its hardware, firmware, and software will dramatically reduce problems and downtime in the future. Proper initial configuration can also save time and reduce issues with upgrades, hot patches, and other changes.
- Monitor the processes and people to know what critical - many of today's enterprises are experiencing a capacity crisis as they reach the limits of reduced budgets, older facilities and legacy infrastructures. Space is tight. Power and cooling resources are over-burdened. Implementing new solutions in inefficient environments may limit their ability to recover from an event. An assessment that examines and analyzes the enterprises environment's capabilities and requirements can provide valuable information to help improve efficiency.
Order DRP BCP Template DRP BCP Sample
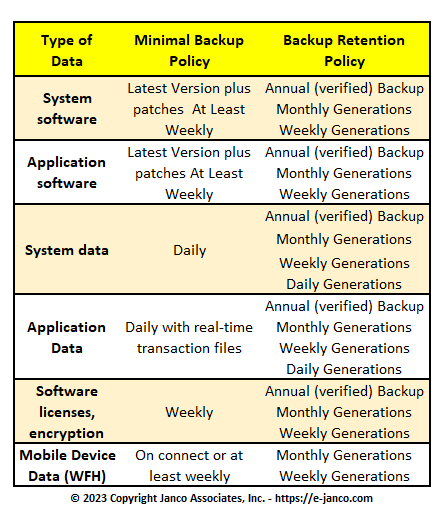
Backup Matrix - Sample from Template
Order DRP BCP Template DRP BCP Sample
Disaster Recovery - Business Continuity Security Bundle
We have just the download you need to create a world class plan and assure you leave no stone unturned. With these Templates we walk you through the entire process, providing all the tools you need along the way. As an added benefit you can purchase an update service which keeps these templates abreast of the latest legislated and mandated requirements. All of our documents have been updated to comply with PCI-DSS, Sarbanes-Oxley, HIPAA, the ISO 27000 (formerly ISO 17799) series - 27001 & 27002, and PCI-DSS.
The Disaster Recovery / Business Continuity and Security Manual Template bundle comes in three versions - Standard, Premium, and Gold.
Order DRP BCP Security Bundle Download Sample