Disaster
Recovery Business Continuity
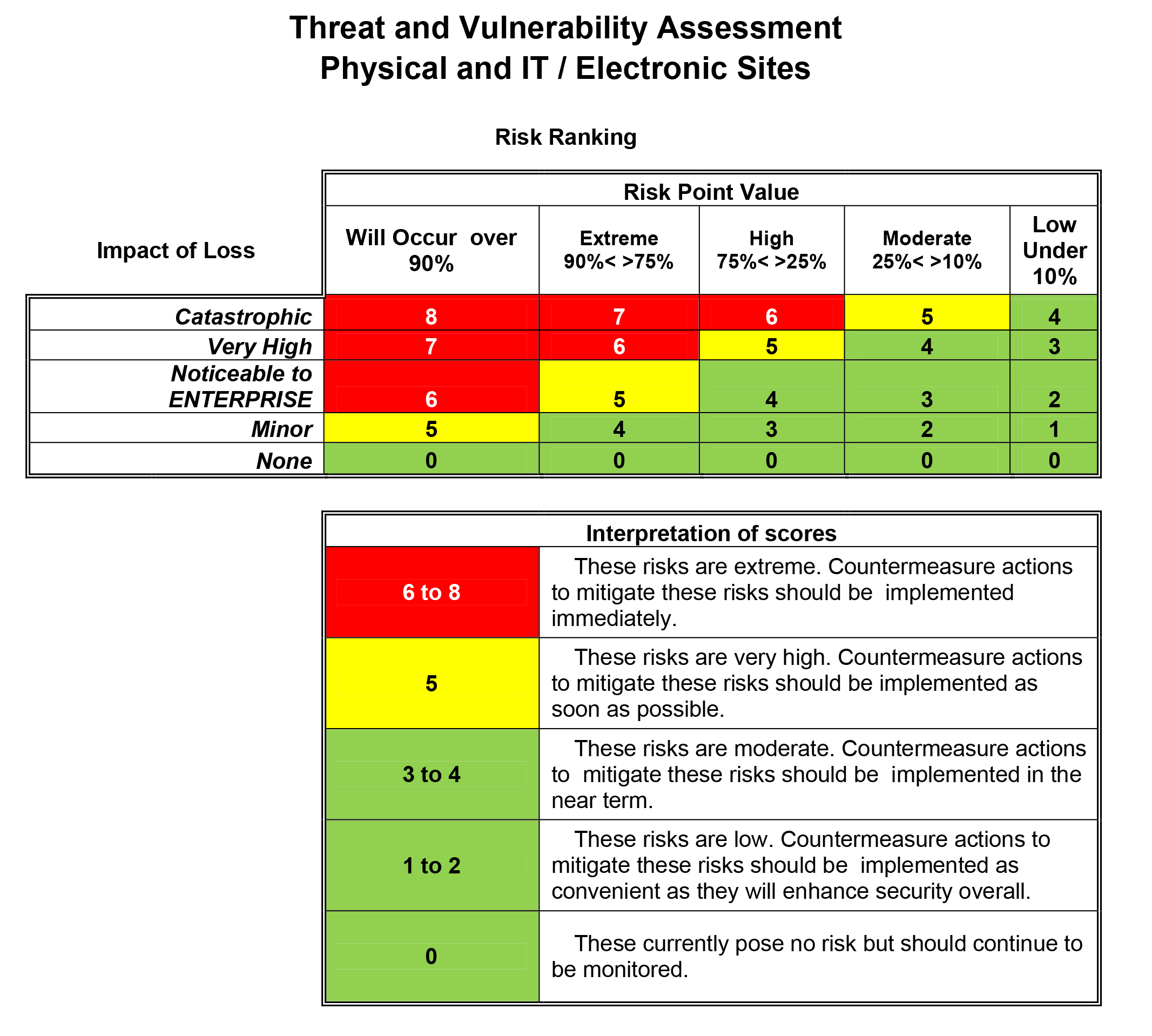
Rating Risk
ITIL Framework to Rate Risk
Order DRP Audit Program Version History Download Sample
Janco has found that over 30% of all Disaster Recovery Business Continuity Plans are in-complete or in-accurate
The typical organization has hundreds of applications all at different recoverability capability. For example some have no plan, some have out of region architectures some have not exercised in long time and some are in great shape testing every quarter.
All of the applications need to be categorizing them so that the Disaster Planning Team can start remediating the ones that place the enterprise at the most risk to the business from both a compliance and readiness perspective.
Using the ITIL framework, you can weigh each Critical Success Factor (CSF) and scoring their Key Performance Indicators (KPI). That allows you to create a rating system and developing a score card report by tiers.
Weighting Critical Success Factors
Examples
- 6 = Critical to success of recovery
- 3 = Required for timely recovery (could recover without but risk is increased)
- 1 = Needed to support recovery but only minimal impact on recovery efforts
Scoring of Key Performance Indicators
Examples
- Not in place or not implemented = 0
- Completed but past the KPI deadline, not accurate or incomplete = 1
- In place or completed on time = 3
- Final rating for each CSF and the associated KPI multiply the weight of the CSF by the score of the KPI
Critical Success Factors/Key Performance Indicators Examples:
- CSF: Conduct exercise at alternate facility (Weight 6)
- KPI = Conduct an annual exercise alternate facility
- CSF: Update BCP Plans (Weight 3)
- KPI = Update BCP plans by <insert date> each year
- CSF: Conduct Annual Tabletop of recovery Plan (Weight 3)
- KPI = Conduct at least 1 annual tabletop of BCP plans by December
Order DR Audit Program Sample DR Audit Program


 Security Audit Program - Self Scoring Tool
Security Audit Program - Self Scoring Tool  DR/BC Audit Program
DR/BC Audit Program







