Top Network Security Weaknesses and Defects Identified
Top Network Security Weaknesses and Defects Identified - After reviewing 152 Security Audit programs Janco has identified the top weaknesses and defects in network security at large and mid-sized enterprises.
Top Network Security Weaknesses and Defects Identified - Janco has review the detail results of 138 security audit programs conducted between September 15, 2008 and January 15, 2010 and identified the top eight defects mentioned inaudit reports.
Victor Janulaitis the CEO of Janco said, "We did not find a single company that had zero security weaknesses or defects reported in their audit reports. The security weakness and defects Janco found were: 1 - Single level verification use on sensitive data (53%; 2 - public workstations connected into secure network (45%); 3 - Shared login used (25%); 4 - Client-side data validation only used for sensitive data(21%); 5 - Access point weak encryption (21%); 6 - Login not encrypted for sensitive data access (17%); 7 - Back-end encryption not utilized (12%); and 8 - Sever Management encryption not utilized (6%).
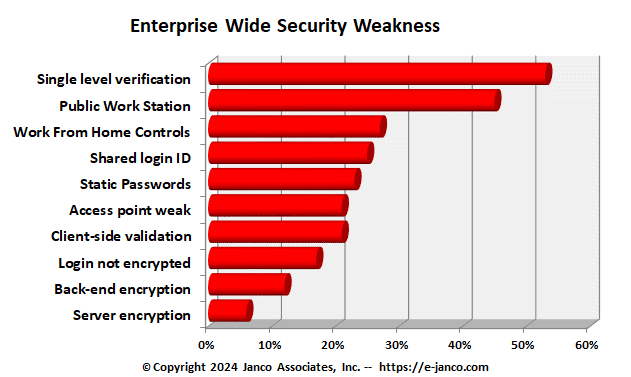
The data was captured by reviewing the detail findings of the audit reports. If there was a single occurrence of the defect it was counted. Janulaitis added, "What was striking was that there are still over one quarter of all enterprises where users share logins. Interestingly, those enterprise that utilize double levels of verifications the number of shared logins drops to a value that is not statistically significant. "
The core document used for the audit programs was the Janco Security Audit Program. Submission of the summary audit program was voluntary and may not be representative of all enterprises.
The Security Manual template includes sections on critical topics like:
- Risk analysis
- Staff member roles
- Physical security
- Electronic Communication (email / Smartphones)
- Blogs and Personal Web Sites
- Facility design, construction and operations
- Media and documentation
- Data and software security
- Network security
- Internet and IT contingency planning
- Insurance
- Outsourced services
- Waiver procedures
- Employee Termination Procedures and Forms
- Incident reporting procedures
- Access control guidelines
- PCI DSS Audit Program as a separate document
- Security Compliance Checklists
- Massachusetts 201 CMR 17 Compliance Checklist
Order Security Manual Template Download Sample
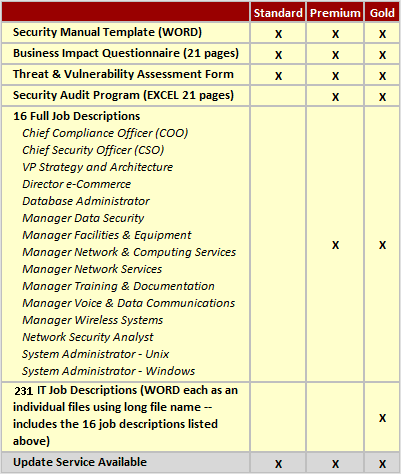
The Security Manual Template can be acquired as a stand alone item (Standard) or in the Premium or Gold sets:
Order Security Manual Template Download Sample




