Data Center Recovery Strategy
A critical component of disaster recovery business continuity is the data center recovery strategy -- Hot Site, Warm Site, Mobile Facilities, Cold Site, Reciprocal Agreement, or Cloud -- Which to choose and why
Which is the best strategy for data center recovery of hot, warm, mobile, and cold sites versus reciprocal agreements?
Hot site
A hot site is a full or partial duplicate for a primary IT operation, including complete computer systems and near-real-time backups for systems, applications and data. In its most expensive form, mirroring software is used to keep a hot backup site and a primary site synchronized. They typically are duplicates of existing data centers.
Warm sites
A warm site is a hot site minus data replication. That is, a warm site offers access to space, utilities and equipment, but requires current backups be installed, and systems and services brought online to become operational. A warm site may be a complete duplicate of an original site, but will typically provide only a subset of mission-critical equipment, services and data.
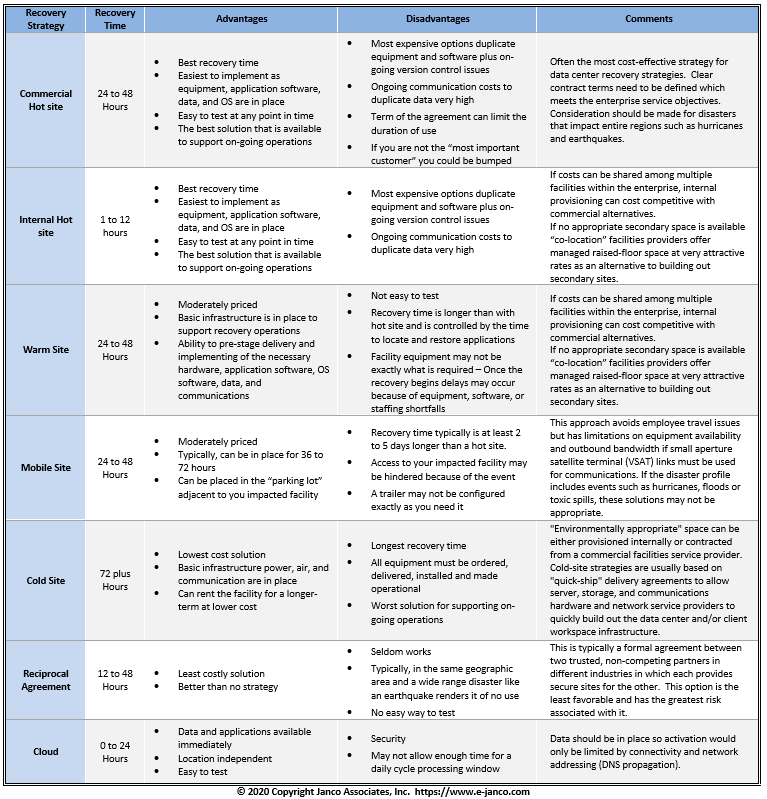
Table extracted from Janco's Disaster Recovery / Business Continuity Template. See DR/BC
Mobile sites
An offshoot of a warm site is a mobile site that consists of trailers that are pre-configured to meet requirements and are flown in, moved by truck are set up in predetermined locations around the country where they can be activated during an emergency
Cold Site
Cold sites which are empty facilities, such as trailers, warehouses, open space in existing data centers specially equipped for emergency use; or simply empty buildings that are wired for power, communications and HVAC but are empty. The cost model for each is quite different.
Cloud
The cloud for some mission critical applications does work well. This includes web hosting and corporate e-mail. Other applications can be run via the web but there would be serious security concerns for sensitive information.
Order DRP BCP Template DRP BCP Sample
Read on Data Center Backup Strategy...
Security Breach on White House Nuclear Computer Data Base
Security is an issue that is critical to the success of everyone -- including the government

White House sources partly confirmed that U.S. government computers - reportedly including systems used by the military for nuclear commands - were breached by Chinese hackers.
“This was a spear phishing attack against an unclassified network,” a White House official told FoxNews.com. “These types of attacks are not infrequent and we have mitigation measures in place. ”
A law enforcement official who works with members of the White House Military Office confirmed the Chinese attack to FoxNews.com on Monday, but it remains unclear what information, if any, was taken or left behind.
“This White House Communications Agency guy opened an email he wasn't supposed to open. ”
Security incidents are rising at an alarming rate every year. As the complexity of the threats increases, so do the security measures required to protect networks and critical enterprise data. CIOs, Data center operators, network administrators, and other IT professionals need to comprehend the basics of security in order to safely deploy and manage data and networks.
Read on Order Security Manual Template Download sample




