Disaster
Recovery
Disaster
Recovery
Business Continuity Audit Program
2026 Edition
ISO 28000 - 27001 - 27002 -22301
HIPAA - SOX - PCI-DSS BYOD and Mobile Devices - IoT
Clockchain - Artifical Intelligence
Order DRP Audit Program Version History Download Sample
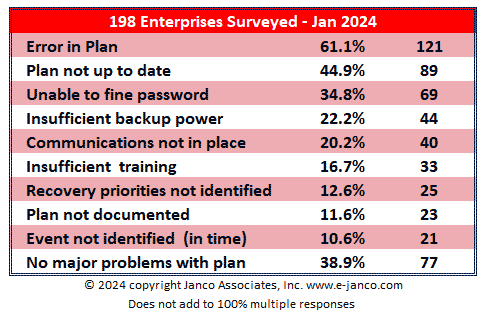
Janco has found that less than 40% of all Disaster Recovery Business Continuity Plans are without a major defect
This Disaster Recovery / Business Continuity Audit program identifies control objectives that are met by the audit program. There are approximately 50 specific items that the audit covers in the 18 page audit program. Included are references to specific Janco products that will assist you in addressing any defects or shortcoming the audit uncovers.
This DR/BC Audit program is the right tool to see that the plans that in place work.
This program can be used as standalone audit program or in concert with the following Janco offerings:
- Disaster Recovery / Business Continuity Template
- Security Manual Template
- Security Audit Program Template
- Business and IT Impact Questionnaire
- IT Service Management for Service Oriented Architecture
- Metrics for the Internet and Information Technology
The Disaster Recovery / Business Continuity Audit program covers the following control objectives are:
- Ensure that adequate and effective contingency plans have been established to support the prompt recovery of crucial enterprise functions and IT facilities in the event of major failure or disaster;
- Ensure that all mandated disaster recovery, business continuity, and security requirements have adequate compliance policies and procedures in place;
- Ensure the survival of the business and to minimize the implications of a major enterprise and/or IT failure;
- Ensure that all the potential risks to the enterprise and its IT facilities are identified and assessed in preparation of the contingency plans;
- Ensure the optimum contingency arrangements are selected and cost effectively provided;
- Ensure that an authorized and documented disaster recovery / business continuity plan is created, maintained up-to-date, and securely stored;
- Ensure that the recovery plan is periodically tested for its relevance and effectiveness;
- Ensure that all internal and external parties to the recovery process are fully aware of their responsibilities and commitments;
- Ensure that appropriate liaison is maintained with external parties (i.e. insurers, emergency services, suppliers, etc. );
- Ensure that both the damaged and recovery sites are secure and that systems are securely operated in support of the enterprise;
- Ensure that systems and procedures are adequately and accurately documented to aid the recovery process; and
- Ensure that public and media relations would be effectively addressed during an emergency in order to minimize adverse publicity and business implications.
Included with this program area Microsoft (.docx format) Word Document and an a PDF version of the Audit Program.
Order DR Audit Program Sample DR Audit Program
See also Rating Disaster Recovery Risk

 DR/BC Audit Program
DR/BC Audit Program


 Security Audit Program - Self Scoring Tool
Security Audit Program - Self Scoring Tool