IT Infrastructure Management -- the Next Challenge
 IT Infrastructure Management -- the Next Challenge - In many enterprises, CIOs are perceived as mere technology managers, while in reality they should beviewed as business leaders. The CIO's focus should be on reducing costs and improving profitability through the strategic usage of IT. It is very important for the Information Technology organization to get out of a transactional mode. If the CIO has the right infrastructure in place, then the CIO can help in directing the strategy of the enterprise, and even shape its destiny. The CIO brings his own perspective, and without IT, you cannot build a robust and business.
IT Infrastructure Management -- the Next Challenge - In many enterprises, CIOs are perceived as mere technology managers, while in reality they should beviewed as business leaders. The CIO's focus should be on reducing costs and improving profitability through the strategic usage of IT. It is very important for the Information Technology organization to get out of a transactional mode. If the CIO has the right infrastructure in place, then the CIO can help in directing the strategy of the enterprise, and even shape its destiny. The CIO brings his own perspective, and without IT, you cannot build a robust and business.
The CIO Infrastructure Management Tool Kit is comprised of a collection of Janco products that CIOs and IT Managers can use to create a strategy and manage in the ever changing business environment.
Or you can get the CIO Infrastructure Policy Bundle which includes the following policies with Electronic forms. The policies have just been updated to comply with all mandated requirements and include electronic forms that can be Emailed, filled out completely on the computer, routed and stored electronically. A totally solution that uses technology at its best.
The policies have just been updated to comply with all mandated requirements and include electronic forms that can be Emailed, filled out completely on the computer, routed and stored electronically -- a total solution.
We have just completed a major update of all the individual polices and all of the electronic forms.
- CIO IT Infrastructure Policy Bundle (All of the policies below are included as individual MS Word files and a single PDF file. Electronic forms are all individual documents that are easily modifiable)
- Backup and Backup Retention Policy
- Blog and Personal Web Site Policy (Includes electronic Blog Compliance Agreement Form)
- BYOD Policy Template (Includes electronic BYOD Access and Use Agreement Form)
- Google Glass Policy (Includes Google Glass Access and Use Agreement Form)
- Incident Communication Plan Policy (Updated to include pandemic considerations and social networks as a communication path)
- Internet, e-mail, Social Networking, Mobile Device, Electronic Communications, and Record Retention Policy(Includes 5 electronic forms to aid in the quick deployment of this policy)
- Mobile Device Access and Use Policy
- Patch Management Policy
- Outsourcing and Cloud Based File Sharing Policy
- Physical and Virtual Server Security Policy
- Privacy Compliance Policy - California Privacy Act
- Record Classification, Management, Retention, and Destruction Policy
- Safety Program (Includes mandated OSHA electronic forms)
- Sensitive Information Policy (CCPA, GDPR & HIPAA Compliant and includes electronic Sensitive Information Policy Compliance Agreement Form)
- Service Level Agreement (SLA) Policy Template with KPI Metrics
- Social Networking Policy (includes electronic form)
- Technology Acquisition Policy
- Text Messaging Sensitive and Confidential Information (includes electronic form)
- Travel, Electronic Meeting, and Off-Site Meeting Policy
- Wearable Device Policy
- WFH & Telecommuting Policy (includes 8 electronic forms to effectively manage work at home staff)
- IT Infrastructure Electronic Forms
Read On Order IT Infrastructure Policies Download Selected Pages
Core Disaster Recovery Business Continuity Assessment
Many businesses have never tested the recovery process in the event of a server or site failure
With business continuity a core component of risk management, a well-rehearsed plan lays the foundation for confidence that IT systems will work when needed most.
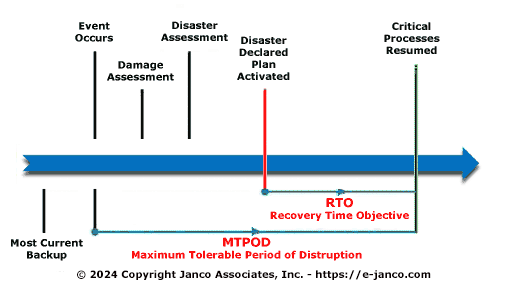
Terms like Maximum Tolerable Period of Disruption (MTPOD), recovery time objective (RTO) and recovery point objective (RPO) are often used, but what do they really mean? In practical terms, recovery time objective is the duration until a business can return to normal after the failure of a server or key computer site, and recovery point objective is the place in the transaction flow where the business resumes.
- Recovery Time Objective (RTO) - How long can your business afford to be down?
- Recovery Point Objective (RPO) - How often do you backup? How much data can your business afford to lose in the event of a disaster?
- Level of Service (LOS) - What are your business' critical servers and essential units that cannot be disrupted?
Implementing a disaster recovery plan includes documenting the process to bring a server or group of servers back online in the event of failure. An overlooked step in the process often flows from the assumption that an IT expert is always readily available. Due to the inherent unpredictability of a disaster, the IT staff that your company relies on may take time to find and start action. Considering this human latency when developing the recovery plan naturally highlights any undesirable complexity in the systems and processes, and the need to support recovery even with minimal IT expertise on hand.
- Core disaster recovery and business assessment questions
- Could a newly hired IT professional quickly handle the situation?
- Could a remote IT engineer talk a novice through the procedures?
- Could a smart phone, tablet, or remote laptop provide all needed access to bring your business back online?
- Could the disaster recovery business continuity plan be executed within the RTO and RPO requirements?
In addition to reviewing your disaster recovery and business continuity plan your team needs to define a realistic picture of their expectations. You could spend too much time thinking of costly alternatives to cover aspects of daily operations that may not be critical. When doing so, ask yourself and your executive team:
- Specifically, what level of protection is necessary (RTO, RPO, LOS)?
- Which aspects of your company's business must stay operational?
All of this is defined in Janco's "Disaster Recovery - Business Continuity Template".
IT Job Descriptions Meet Compliance Requirements
 ISO (including 27031), HIPAA, Sarbanes-Oxley, PCI-DSS, California SB 1386, and Cobit requirements are meet by Internet and IT Position Descriptions. . .
ISO (including 27031), HIPAA, Sarbanes-Oxley, PCI-DSS, California SB 1386, and Cobit requirements are meet by Internet and IT Position Descriptions. . .
The Internet and IT Position Descriptions HandiGuide™ was completed in and is over 900 plus pages; which includes sample organization charts, a job progression matrix, and 243 Internet and IT job descriptions. The book also addresses Fair Labor Standards, the ADA, and is in a new easier to read format. To see the what has changed go to our version history.
You can purchase either the book with all of the job descriptions in PDF format or the book in PDF format and the job descriptions in MS WORD format, or just the job description in MS WORD format.
Order IT Job Description HandiGuide Sample Description Download TOC
Record Classification, Management, Retention, and Destruction policy Critical for Security
Template includes citation for federal and selected state record retention requirements
 All business are required by law to keep confidential client information, as well as employee or company data for a minimum amount of time. There are numerous business records that should be held on to for a minimum of seven years, which can include employee agreements, business loan documentation, litigation records, as well as general expense reports and records including overhead expenses and professional consultation fees.
All business are required by law to keep confidential client information, as well as employee or company data for a minimum amount of time. There are numerous business records that should be held on to for a minimum of seven years, which can include employee agreements, business loan documentation, litigation records, as well as general expense reports and records including overhead expenses and professional consultation fees.
Other documents may be kept for shorter, longer or an indefinite period of time and it's important to know what legal requirements are enforced for your industry to not only stay compliant, but to also dispose of documents you may no longer need. Regularly maintaining filing cabinets and securely disposing of old documents can help minimize risk of sensitive information falling into the wrong hands. The risks of keeping old documents containing sensitive data can be high - resulting in identity theft, fraud and potential financial loss or reputation damage.
Read On Order Record Management Policy Download Selected Pages