Biometric Security Options
Passwords are not as secure as biometric identifiers and over time will be replaced
Passwords will slowly give way to biometrics. Currently computers and other devices have cameras, scanning capabilities, and AI capabilities which will make this shift possible.
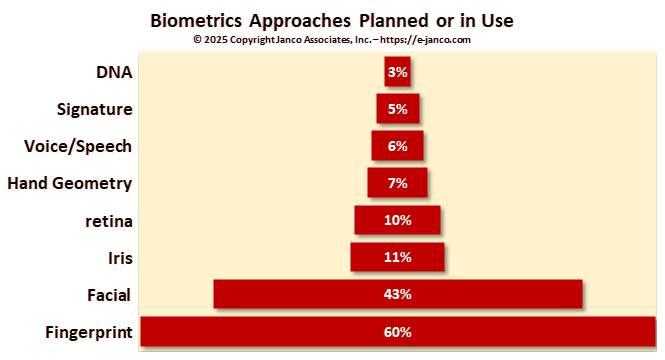
Biometrics can be easily and accurately tied to a single individual. They do not have to be tied to any specific device. Rather they can be stored on the device itself or on an encrypted server and accessed whenever that individual needs access or use to the device, database, application, or use. There are eight that are or will be in use soon.
- Fingerprint recognition – Fingerprints have been in use as an identified for over 100 years. With the onset of low-cost scanners on everyday use devices like SmartPhones, tablets, desktops, and physical access panels, they are the most common biometric reader. In a recent report, it was found that fingerprint scanning is used by over 60% of all US and EU-based enterprises and 85% of individuals who have SmartPhones. The fingerprint data can be stored on the device itself or an encrypted server. In the case of the latter, there are security and privacy issues.
- Facial recognition - If a device is equipped with a camera, it can easily be used for authentication. Facial recognition is the easiest common approach. However, if a face is partially covered, facial recognition fails. That was the case during the latest pandemic.
- Iris recognition – A video camera analyzes the iris characteristics including rings, furrows, freckles that are situated in the colored tissue around the pupil. Typically, this works thru glasses and contact lenses.
- Retina recognition – Infrared camera is used to capture the unique patterns of an individual’s retina blood vessels.
- Hand geometry recognition – A hand geometry reader measures an individual’s hand in several dimensions. Then, it stores the data for further comparison and measurement.
- Voice/speech recognition - Voice-based digital assistants and telephone-based service portals are already using voice recognition to identify users and authenticate customers. According to our study, some companies use voice recognition for authentication within the enterprise.
- Signature recognition - Digital signature scanners are already in widespread use at retail checkouts and in banks and are a good choice for situations where users and customers are already expecting to have to sign their names.
- DNA recognition - Today, DNA scans are used primarily in law enforcement to identify suspects. In practice, DNA sequencing has been too slow for widespread use. This is starting to change. A $1,000 scanner is now available that can do a DNA match in minutes.
How secure is biometric authentication data?
A local authentication mechanism is the hardware security module in a SmartPhone. User information - such as a fingerprint scan, facial image, or a voice-print - is stored inside the module. When authentication is required, biometric information is collected by the fingerprint reader, camera, or microphone and sent to the module where it is compared to the original. The module tells the phone whether or not the new information is a match to what it already had stored.
With this system, the raw biometric information is never accessible to any software or system outside the module, including the phone's operating system.
Enterprises can also use SmartPhone-based biometric readers whenever their users or customers have access to SmartPhones, without ever having to collect and store any identifying biometric information on their servers. Similar technology is available for other types of devices, such as smart cards, smart door locks, or fingerprint scanners for PCs.
The security of the biometric authentication data is even more important than the security of passwords. Passwords can be easily changed if they are exposed. A fingerprint or retinal scan, however, is not changeable. The release of this or other biometric information could put users at permanent risk and create significant legal exposure for the company that loses the data.
If a company collects authentication information and keeps it on its servers, best-practice security measures need to be applied. That includes encryption for both data at rest and data in transit. There are solutions for runtime encryption, which keeps the data in encrypted form even while it is being used.
Encryption is not a guarantee of security. If the applications or users that are authorized to access the data are themselves compromised, then there is an issue.
In the event of a breach, it creates a challenge because physical attributions such as fingerprints cannot be replaced. Biometric data in the hands of a corrupt entity, perhaps a government, carries very frightening but real implications as well.
Read on Order Security Manual Template Download sample

