Malware Impact on Security - Increasing Threat
Malware Impact on Security - Malware infections cause a number of problems. Machines become unresponsive or sluggish resulting in users become frustrated and administrators spending precious time trying to find the problem. When a machine is infected, some administrators often want to simply re-install the operating system, however a responsible system administrator or security analyst would want to investigate and assess the situation before doing anything else. All of these tasks take time and resources. People have to stop working, the hardware has to be replaced and so on. Additionally, some malware creates a denial of service by design, increasing the possibility of an attack on the organization's infrastructure.
Order Security Manual Template Download Sample
While most organizations understand denial of service very well - since it impacts productivity - many ignore the impact on confidentiality and integrity. Attackers are known to harvest sensitive information from compromised computers to carry out further and deeper attacks within the network. If they access the organization's data they can use this to sell to third parties and make a profit. Modern malware can create an automated process to harvest information from a network that has been breached.
Once an attacker is on the inside, his or her work is significantly easier since on most networks, systems on the inside are trusted. This is what makes attacking web visitors through infected websites so attractive to the bad guys. End-users and their web browsers are already on the internal network. Unlike traditional network-based attacks, the victim connects to the attacker instead of the other way round. Even today, most defenses are still focused on preventing attackers from trying to connect to the victim, i.e. protecting the perimeter.
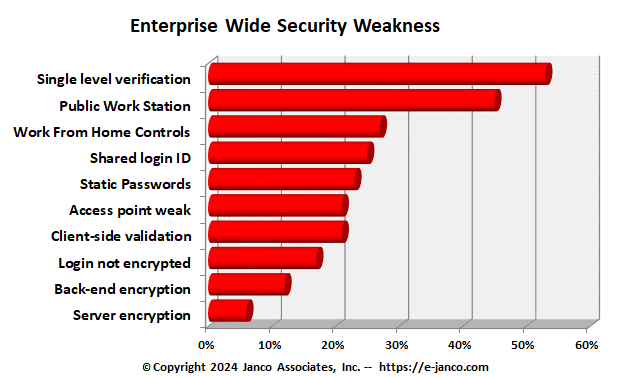
Security Weakness
In a review of 138 enterprise audits Janco has identified top security flaws in “enterprise” web sites.
The most common security mistakes that are made on corporate web sites have been identified Janco Associates of Park City, UT.
They are:
- Using only single level verification for access to sensitive data - Password authentication is more easily cracked than cryptographic key-based authentication. The purpose of a password is to make it easier to remember the login credentials needed to access a secure resource, however biometric or key-based authentication is a stronger authentication method which make credential more difficult to crack.
- Having “public” workstations or access point is connected to a secure network - If workstation that anyone can use or re-boot is connected to a secure resource you can't guarantee it is secure. Keyloggers, compromised network encryption clients, and other tricks of the malicious security cracker's trade can all allow someone unauthorized access to sensitive data regardless of all the secured networks, encrypted communications, and other networking protections you employ.
- Sharing login credentials - The more login credentials are shared, the more they likely they are commonly know by too many others, even with people who should not have access to the system. The more they are shared, the more difficult it is to establish an audit trail to help track down the source of a problem. The more they are shared, the greater the number of people affected when logins need to be changed due to a security breach or threat.
- Data validation for forms is contained in client-side JavaScript - A malicious security cracker can develop a form that accesses the resource at the other end of the Web page's form action that does not include any validation at all. In addition, JavaScript form validation can be circumvented simply by deactivating JavaScript in the browser or using a Web browser that does not support JavaScript at all. Server-side validation does not fall prey to the shortcomings of client-side validation because a malicious security cracker must already have gained access to the server to be able to compromise it.
- Connect to network from an unsecure access point - When traveling avoid connecting from open WiFi networks, networks with unknown or uncertain security characteristics or from those with known poor security such wireless access points in coffee shops. This is especially important whenever you must log in to the server or Web site for administrative purposes or otherwise access secure resources. If you must access the Web site or Web server when connected to an unsecured network, use a secure proxy so that your connection to the secure resource comes from a proxy on a secured network.
- Corporate web site is encrypted but the login process is not - Encrypting a session after login may be useful but failing to encrypt logins is a bit like leaving the key in the lock when you are done locking the barn door. Even if a login form POSTs to an encrypted resource, in many cases this can be circumvented by a malicious security cracker who develops their own login form to access the same resource and allow them access to sensitive data.
- Using weak encryption for back end management - Using Windows Remote Desktop without and encrypted user-id and password in a non-VPN environment is opening your site to the world. Using proprietary platform-specific technologies often leads to resistance to use of secure encryption for Web site access. Cross-platform-compatible strong encryption such as SSH is usually preferable to platform-specific, weaker encryption tools such as Windows Remote Desktop.
- Using unencrypted or weak encryption for Web site or Web server management- Using unencrypted connections (or even connections using only weak encryption), such as unencrypted FTP or HTTP for Web site or Web server management, opens you up to man-in-the-middle attacks and login/password sniffing. Use encrypted protocols such as SSH to access secure resources, using verifiably secure tools. . Once someone has intercepted your login and password information, that person can do anything you could have done.
Order Security Manual Template Download sample Version History