Steps to Detect and Prevent Security Breaches
Five actions that CIOs and CTOs can take. . .
One of the greatest assets of the vast majority of organizations consists of digital bits of information, not their physical holdings. Increasingly, data stored in databases, file management systems, flat files, spreadsheets, and other information storage formats is the linchpin for enterprise success. Intellectual property, transactions, and records to name a few are fueling business because that information is the currency upon which business operations function. Organizations are creating and using data at an unprecedented level, as represented in the demand for storage capacity.
According to independent studies, the annual capacity growth rates for the storage of data within enterprises grew 47%. The creation and processing of critical information won't let up anytime soon. Mandates for electronic health records and smart utility grids are just a few examples of what will accelerate the information explosion in the years ahead. Businesses have become more dependent on information. The gathering, organizing, managing, finding, and analyzing of information are now crucial to most businesses. Information manipulation can make a business more flexible and better able to address emerging business trends. As information usage proliferates among more and more users, organizations must deliver data to only those who require it for their jobs. Data accessibility, to authorized users, is at the heart of business processes. The proper management of the data is the purview of databases.
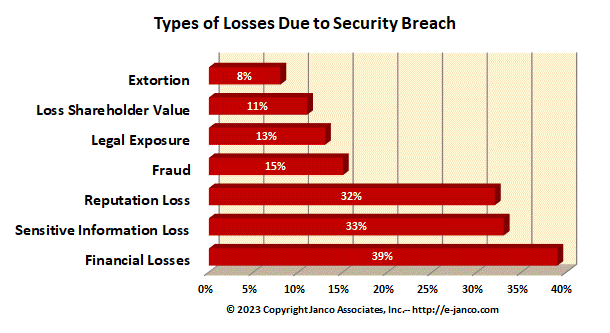
Types of losses due to Cyber-Attacks and Security Breaches
As the value of information collected, organized, manipulated, and analyzed grows, so do the threats to that data. Any organization with sensitive personal or financial data represents a potential target. New attack vectors are aimed at siphoning off the critical data while avoiding detection. Criminal elements are conducting targeted attacks on the "information business jugular" of financial assets, sensitive proprietary data, or resalable personal data. Authorized insiders also contribute to data breaches by either intentionally taking data or inadvertently releasing data.
How do you defend against system attacks and security breaches? Janco Associates has defined a set of steps that enterprises of all sizes can follow to help to achieve a safe and secure computing environment. The steps that CIOs and CSOs should follow are:
- Access the network and computing environment - Have an inventory of all devices, accesses points, security protocols, encryption levels, programs, and users. This inventory should have limited distribution and should be reviewed and updated frequently (at least quarterly).
- Conduct in-depth system and network security audits -Test and validate that only the authorized items are running on the systems and network. Create and review in-depth logs files to monitor compliance to security protocols, violation alerts, and actions taken.
- Establish network access rules that allow on valid access - Close all un-used ports on routers and disable all unused user ids and passwords. Implement a "two-factor" authentication and encryption process for all sessions. Require all users to use "two-factor" authentication. On the third authentication violation within a specified period, disable the device, port, or user from the system and network.
- Mechanize and retain detail logs - Record everything possible including dates with full timestamps and implement firewalls that minimize inbound attacks. Review these logs in detail daily and report at least weekly to the CIO or CSO the types of issues that occur.
- Assume someone is attacking you now - Use the logs in a comparative way to see differences between prior periods and the current period to identify how someone could be getting into the system and network. Have outside third parties try to break in - see if you can identify and block them.
Order Security Manual Template Download sample Version History
The Security Manual Template can be acquired as a stand alone item (Standard) or in the Premium or Gold sets:
Order Security Manual Template Download sample Version History