How to prepare before a cyberattack occurs
CIOs and CSOs are on the frontline of cyberattack defense
Order Security Manual Template Download sample Version History
As the ongoing changes in the business environment continue, CIOs and CSOs are driving the Security Management processes to address both cyberattacks and compliance with mandates. We have identified several common processes that “World-Class” CIOs and CSOs follow.1. Know what the enterprise’s exposures are
CIOs and CSOs need to understand what digital assets are exposed, where attackers will most likely target a network, and what protections are required. Increasing data and security visibility and building a strong representation of vulnerabilities is critical. Common vulnerabilities include older and less secure computers or servers, unpatched systems, outdated applications, and exposed IoT devices.
Predictive modeling can help create a realistic depiction of possible events and their risks, further strengthening defense and proactive measures. Once the risks are understood, the enterprise can model what will happen before, during, and after an event or breach. Included in what to look for are:
- What kind of financial loss can you expect?
- What will be the reputational damage of the event?
- Will you lose business intelligence, trade secrets, or more?
Know what the defense is protecting (accurate asset inventory); monitor for vulnerabilities in those assets; and use threat intelligence to know how attackers are going after those assets with those vulnerabilities. To answer each of those three questions skilled staff with security and enterprise operational backgrounds are required.
2. Minimize risk vulnerabilities
Once an enterprise knows what its risk vulnerabilities are, it can then take actions to mitigate the risk posed by the most significant vulnerabilities and potential attack vectors before moving on to lower-priority tasks. Bringing assets offline where possible and strengthening internal and outward-facing networks are two key areas to focus on.
Most networks offer tools to help minimize the attack surface. For example, Microsoft’s Attack Surface Reduction (ASR) rules allow you to block processes and executables that attackers commonly use.
We have found that over 50% of security risks are associated with internal staff. A primary defense is to build awareness and train employees to minimize risk vulnerabilities. Questions to ask are:
- What policies does the enterprise have to help stay on top of employee security at home and at-work security?
- Do employees understand what’s required?
- What are the security practices employees should be using, and how could a failure affect them and the business at large?
Not all vulnerabilities need to be addressed and some will persist regardless. A reliable cybersecurity strategy includes methods to identify the most pertinent sources, picking out which are more likely to be exploited. Those are the vulnerabilities that should be mitigated and monitored.
Most businesses allow more access than is needed for employees and contractors. Adequately scoped permissions can ensure there are no disruptions or major damage even when an account is compromised. Start your analysis of access rights with critical systems and then limit each person’s and device’s access to only those assets they absolutely need.
3. Establish strong security practices and policies
Basic steps include implementing intrusion detection solutions, conducting regular risk assessments, and putting clear and effective policies in place. Here are some practices to consider:
- Conduct audits of account management with a focus on strong authentication protocols and access controls.
- Establish consistent version control and patching policies.
- Maintain and test backups of critical data.
- Segment your network to minimize damage should a breach occur.
- Monitor and retire old equipment, devices, and services.
- Use encryption wherever practical.
- Establish or limit your BYOD policies and programs.
4. Establish security monitoring and testing protocols
A “world-class” cybersecurity program requires constant adjustment as IT infrastructures change and threat actors evolve. Focus on continuous monitoring and regular testing. Utilize third-party penetration testing services to achieve this goal.
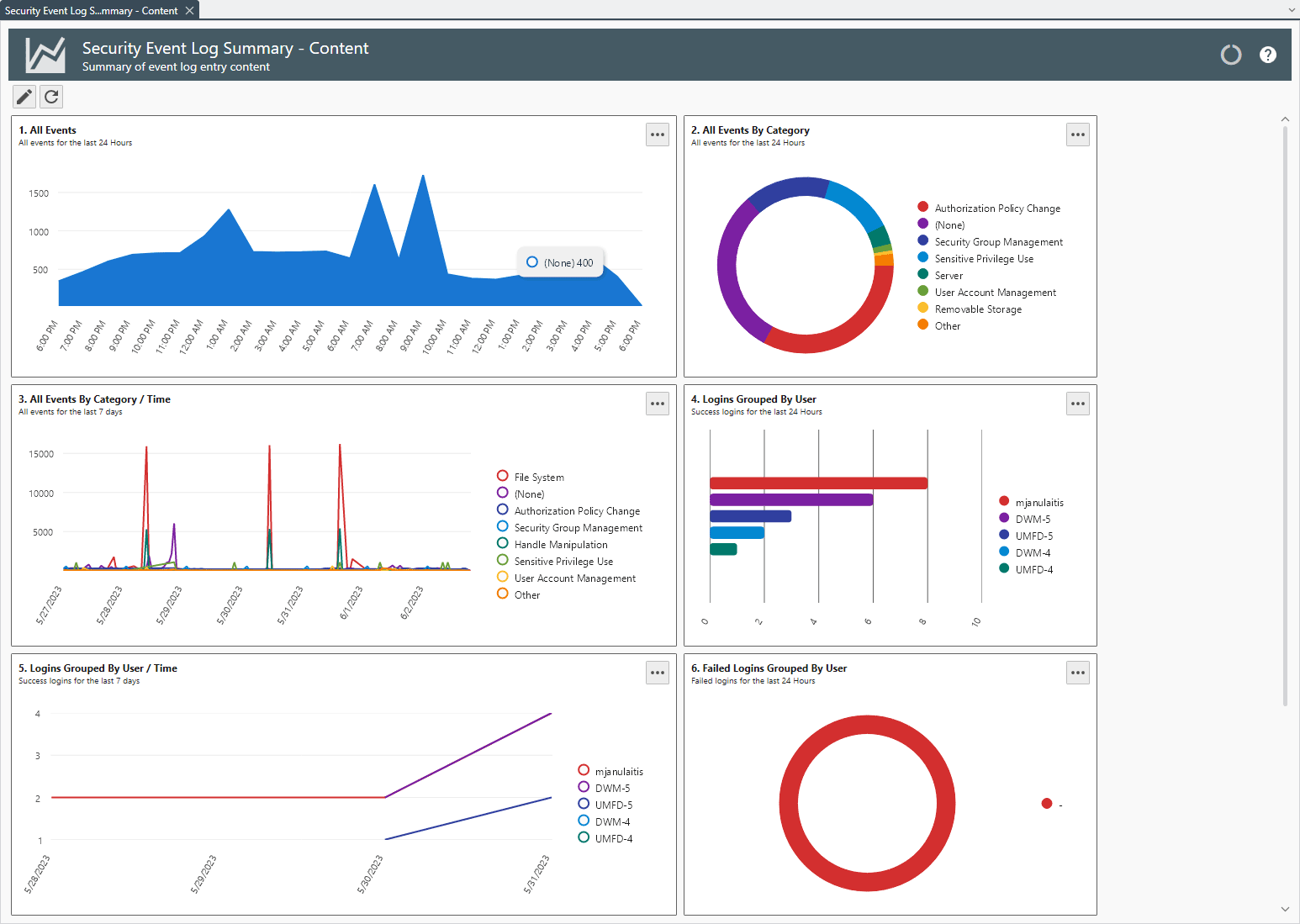
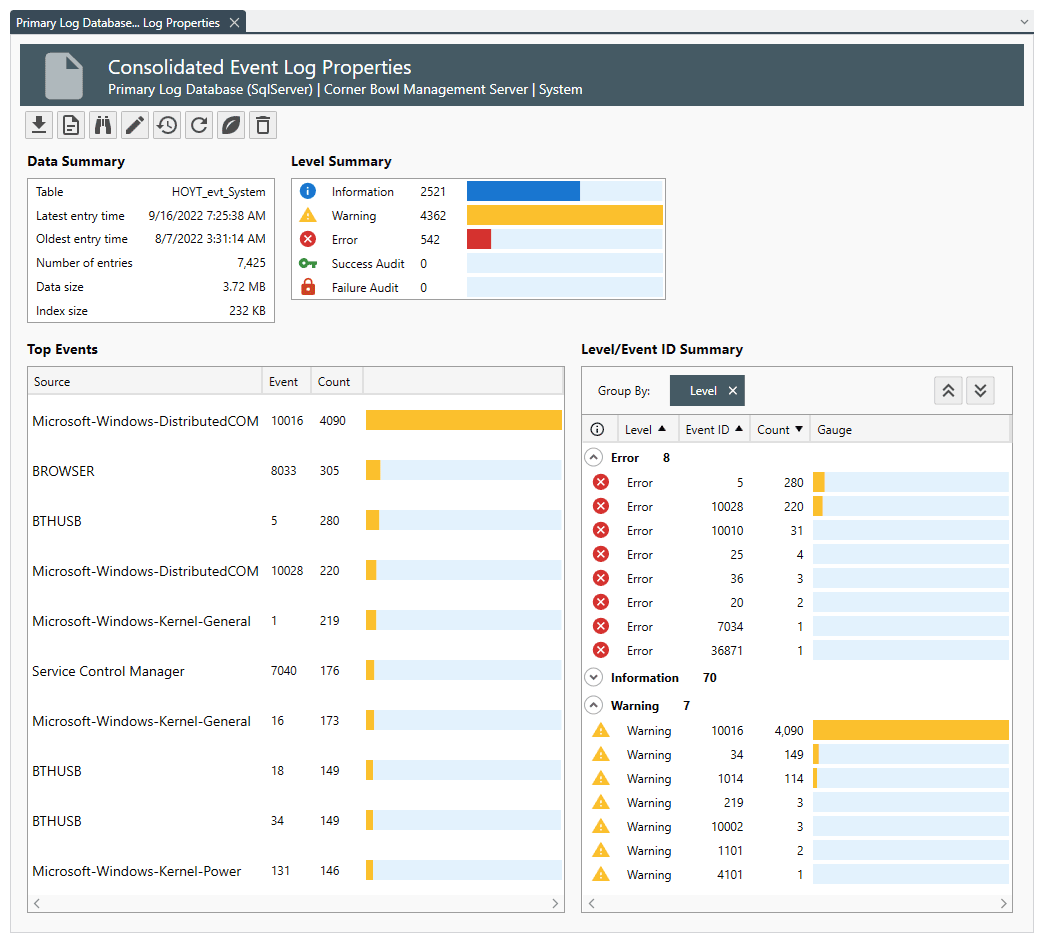
Monitoring is typically done through an automated system like security information and event management software (SIEM). A good solution can be software like Cornerbowl Software https://www.cornerbowlsoftware.com/. It collects log data generated from host systems and applications to network and security devices such as firewalls and antivirus filters. The software identifies, categorizes, and analyzes incidents and events, as well as analyzes them.
With third-party penetration testing the enterprise gets unbiased third-party feedback to help better understand vulnerabilities. Penetration testers conduct simulated attacks designed to reveal critical vulnerabilities. Testing should touch on core elements of the enterprise network and BYOD and third-party devices vendors are using. Mobile devices account for about 60% of interactions with corporate data.
5. Harden your email and Messaging systems
The Most common way for attackers to compromise networks is via phishing. Many organizations have not fully deployed email and messaging protocols designed to limit the number of malicious emails that employees receive. The protocols are:
- Sender Policy Framework (SPF) prevents spoofing legitimate email return addresses.
- Domain Keys Identified Mail (DKIM) prevents spoofing of the “display from” email address, which is what the recipient sees when they preview or open a message.
- Domain-Based Message Authentication, Reporting, and Conformance (DMARC) allow enterprises to set rules about how to treat failed or spoofed emails identified by SPF or DKIM.
6. Understand compliance
All organizations should have policies and procedures in place to research, identify and understand both internal and government standards. The goal is to ensure all security policies comply and that there’s a proper response plan to the various attack and breach types.
Compliance management requires establishing a task force and strategy for reviewing new policies and regulations when they come into play. As critical as compliance is to modern cybersecurity strategies, it doesn’t necessarily mean it will guarantee the safety of your data.
Compliance management strategies should first assess risk and deploy processes or controls to protect the company and its customers. Then, the enterprise can produce the documentation required by various compliance regimes (such as HIPAA or PCI) showing how your strategy is compliant.
7. Hire auditors
Hiring security auditors and analysts can help you discover attack vectors and risk vulnerabilities that might have otherwise gone unnoticed.
They can also assist in expanding strategies for compliance management on how to deal with potential breaches and attacks. Too many organizations are unprepared for cybersecurity attacks because they didn’t have checks and balances to measure their policies.
When attempting to objectively determine the security risk, having an outside, impartial perspective can be extremely beneficial.
Order Security Manual Template Download Sample