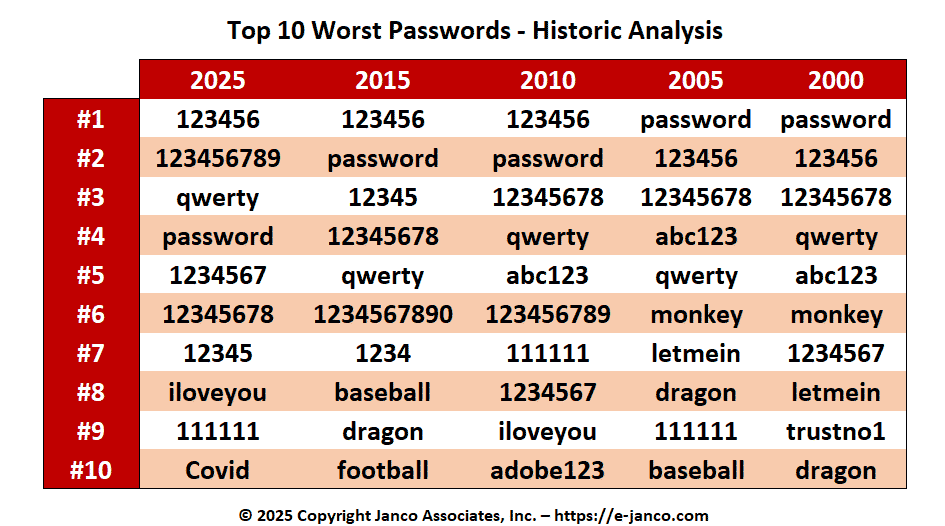
Top 10 Worst Passwords - 21 year history easy to hack
Over the past twenty-one years users have continued to use almost the same worst passwords to access secure systems
Top 10 worst passwords - Traditionally passwords are the first line of defense in securing systems, yet users continue to circumvent that basic security by using the same easily hacked passwords.
Read on Order Security Manual Template Download sample
Until passwords are no longer required as bio-metrics like a fingerprint, facial scans, and retina readers are implemented there is no choice but to utilize them. The question is as passwords become more complex, how long will it take before users rebel and use the same password on multiple sites, have lists of them in unencrypted files on their computers.
Passwords should be at least eight characters in length using number, lower case letters and uppercase letters. Below is a list of the historic top 10 worst passwords that Janco has found users continue to use. As can see the same ones appear year after year.
In order to counter this here are 6 easy rules that can be implemented in your password routines. This will minimize the risk that your users will use these easily hacked weak passwords.
- Require passwords to be 8 character in length with at least one uppercase letter, at least one lowercase letter, and at least one character
- Include in the list of unacceptable passwords the ones list above.
- Move towards biometric passwords or dual step authorization for access to systems.
- Do not allow users to use a previous password when a password reset is done.
- Do not allow the same password to be used by multiple users in the organization.
- Once an employee leaves see that his/her password is eliminated and see that all of the passwords in that "area" are changed in a timely manner.
Protecting and Securing Data Assets
If your company's security processes are disclosed, the company's systems are is vulnerable and sensitive data is at risk. Expanding on the list above, generic standards and procedures to protect the company's electronic assets include encryption keys, user id's, and passwords:
- Restrict access to the fewest number of individuals as possible.
- Store electronic versions only on servers that can be assessed by individuals with the highest degree of administrative security.
- Fully implement and document all management process and procedures
- Generate strong keys, user ids, and passwords,
- In the case of lost electronic keys use a process that requires 2 or 3 people, each knowing only their part of the key to reconstruct the whole key,
- Secure storage and distribution
- Periodically change keys and passwords (at least once every quarter and when there is a seminal change caused by key employee turnover or other such events),
- Dispose of unused ones (e.g. when an employee is terminated all of the keys, user ids, and passwords should be made inactive immediately - not the next day),
- Eliminate the ability of one individual using the key or user id of another, and
- Replace any key that is suspected of being compromised and immediately void the potentially compromised key.
Read on Order Security Manual Template Download sample