Security Manual Template and Compliance Tools
Security Manual - AI Security Management - GDPR Compliance
 Security and compliance are key to maintaining control of sensitive and confidential information. All of the product offerings of Janco are geared toward providing tools to help C-level executives and top IT professionals maintain the privacy of their users and enterprise data. Each of these offerings is current and is updated at least once every three or four months. To support that Janco offers update services for its security and compliance products.
Security and compliance are key to maintaining control of sensitive and confidential information. All of the product offerings of Janco are geared toward providing tools to help C-level executives and top IT professionals maintain the privacy of their users and enterprise data. Each of these offerings is current and is updated at least once every three or four months. To support that Janco offers update services for its security and compliance products.
The premium edition includes 27 full security job descriptions including Data Protection Officer necessary for GDPR compliance.
Read on Order Security Manual Template Download sample
Security Policies - Procedures - Audit Tools - AI Security Management
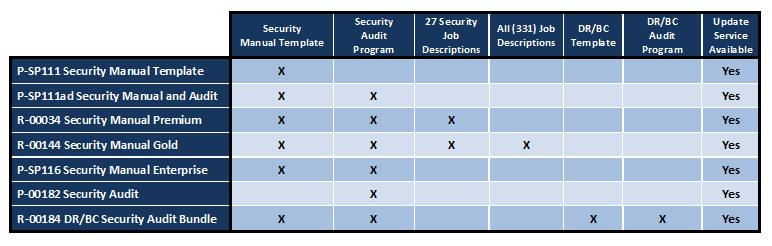
- Security Manual Template (Policies and Procedures) (ISO Compliant)
see also Security Manual Features - Security Forms
- Security Manual Template and Audit Program
- Security Manual Template and Disaster Recovery Business Continuity Template Bundle
- Security Manual Template, Disaster Recovery Business Continuity Template, and Safety Program Bundle
- Security Manual Template and Disaster Recovery Business Continuity Template Audit Bundle
- Security Management Team Job Description Bundle - 27 full security job descriptions
- USA Freedom Act Security Bundle
- Payment Card Industry (PCI) Data Security Audit Program
- Payment Card Industry (PCI) Data Security Standard PCI-DSS Compliance Kit
- Security Audit Program
- Sarbanes Oxley Compliance
- Compliance with HIPAA Standards
- Compliance with FIPS 199
- Threat and Vulnerability Assessment
- Threat Risk Assessment Process
Order Security Manual Template Download Sample
Security Policies are Comprehensive, Detailed and Customizable for Your Business

AI Security Management
The IT Security Manual Template provides CIOs, CSOs, and IT Managers all of the essential materials with real live use-able text for a complete security manual. Detailed language addressing more than a dozen security topics is included in a 260 plus page Microsoft Word document, which you can modify as much or as little as you need to fit your business requirements.
Addresses AI Security Management, WFH security, and includes full job descriptions for Chief Compliance Officer, Chief Security Officer, Data Protection Officer, Manager Security and Workstations, Manager WFH Support, Security Architect, and Systems Administrator.
The template includes sections on critical topics like:
- Risk analysis, Staff member roles, Physical security, Electronic Communication (email / SmartPhones), Blogs and Personal Web Sites, Facility design, construction and operations, Media and documentation, Data and software security, Network security, Internet and IT contingency planning, Insurance, Outsourced services, Waiver procedures, Employee Termination Procedures and Form, Incident reporting procedures, Access control guidelines, PCI DSS Audit Program as a separate document, Massachusetts Compliance Check List, Security Compliance Check List, and update service
Electronic forms that can be Emailed, completed via a computer or tablet, and stored electronically including:
- Blog Policy Compliance, BYOD Access and Use . Company Asset Employee Control Log, Email - Employee Acknowledgment, Employee Termination Checklist, FIPS 199 Assessment, Internet Access Request, Internet Use Approval, Internet & Electronic Communication - Employee Acknowledgment, Mobile Device Access and Use Agreement, Employee Security Acknowledgment Release, Preliminary Security Audit Checklist, Security Access Application, Security Audit Report, Security Violation Reporting, and Sensitive Information Policy Compliance Agreement
Order Security Manual Template Download Sample




